EdgeSense
Contents
- 1 Introduction
- 2 Cloud
- 2.1 EnSaaS
- 2.2 Azure
- 2.3 AWS
- 2.3.1 Node-Red
- 2.3.2 Greengrass
- 2.3.2.1 Prerequisites
- 2.3.2.2 Create Greengrass Group
- 2.3.2.3 Setup Greengrass Group
- 2.3.2.4 Run Greengrass core in your device
- 2.3.2.5 Deploy your Greengrass group
- 2.3.2.6 Set up your AWS IoT Things
- 2.3.2.7 Install your thing certificates
- 2.3.2.8 Configure the samples
- 2.3.2.9 Run the protocol connector sample
- 3 Edge Sense
- 4 Release
Introduction
WISE-PaaS/EdgeSense is an edge intelligence and sensing integration software solution that incorporates sensor data aggregation, cloud applications, edge analytics, and secure end-to-end data protection for fast and easy device-to-cloud operation. “Protocol Connector” is one of the major part of EdgeSense, it is an all-in-one message broker service which collects sensor data via various industrial protocols and then upload to cloud.
Cloud
EnSaaS
Register account on EdgesSense Portal
- Purpose:
Instructions in this document are intended to walk you through on how to register and create a user account on WISE-PaaS/EdgeSense portal
- Steps:
Step 1:
- Step 1-1: Head to WISE-PaaS/EdgeSense portal http://portal-rmm.wise-paas.com
- Step 1-2: Click “Sign up” at the bottom
Step 2
- Step 2-1: Fill in information including “Email”, “First Name”, “Last Name” and “Phone Number”
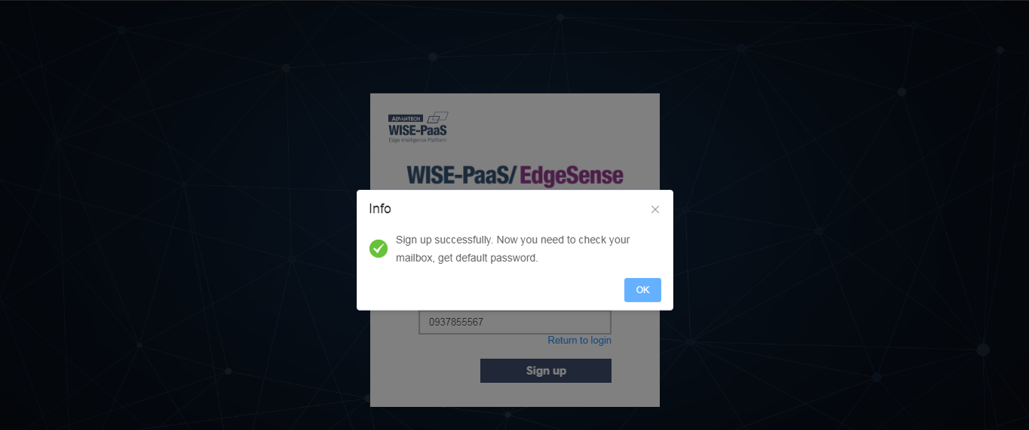
- Step 2-2: A message box will pop up after clicking “Sign up”, indicating it’s successfully done
Step 3:
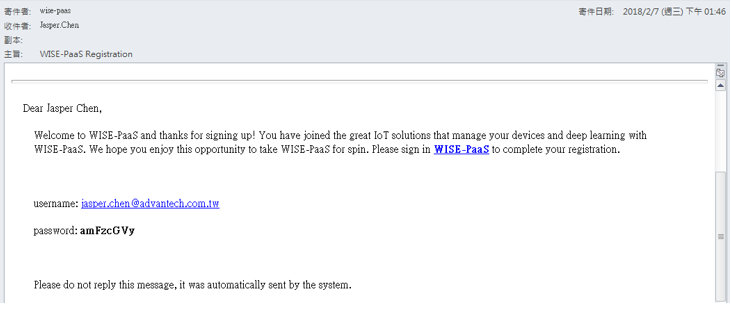
- Step 3-1: In no time, you will receive a welcome email from Advantech in your registred mailbox which contains the information of your username and default password
- Step 3-2: Go back to login portal (as specified in Step1-1 or click “Return to login”) and login with your username and default password provided in welcome email
- Step 3-3: Upon first login, EdgeSense portal will ask user to change default password
- Step 3-4: After changing password, re-login with new password
- Step 3-5: Now you should be able to see default page after logging in WISE-PaaS/EdgeSense portal
How to Connect Edge Devices to RMM Cloud
- Purpose:
Instructions in this document are intended to walk you through the process of connecting your edge devices to RMM cloud
- Steps:
Step 1: Sign in EdgeSense Portal
(If you don’t have an EdgeSense account, please register one by clicking “Sign up” at the bottom)
Step 2: Obtain Agent Credentials and Download EI Agent
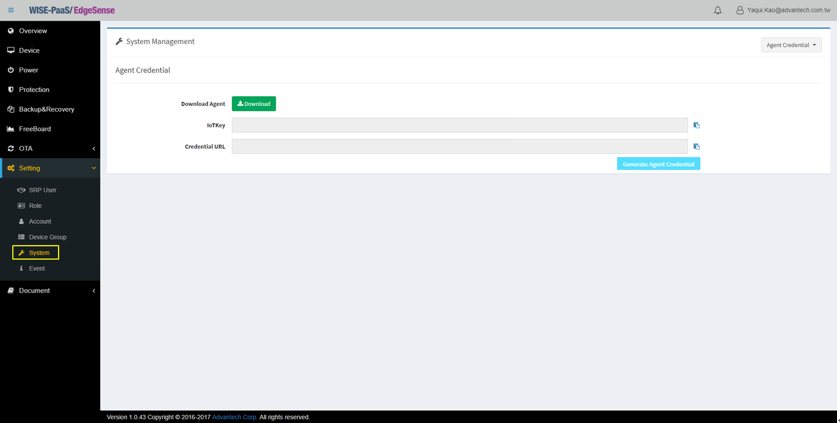
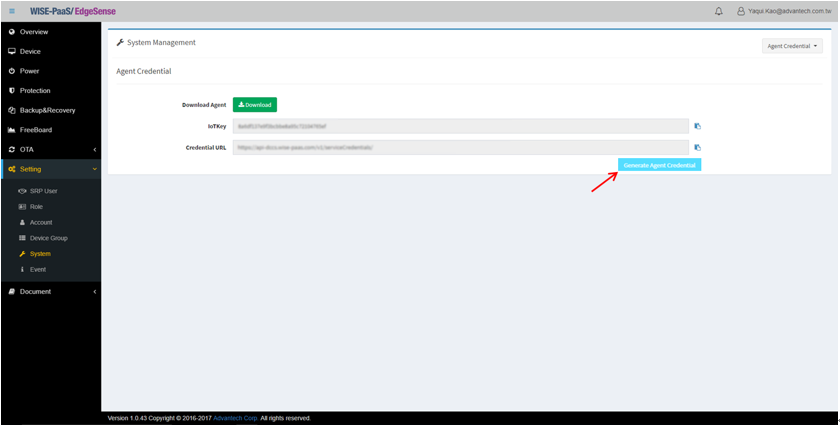
- Step 2-1: Select “System” tab under “Setting” on the left of management console
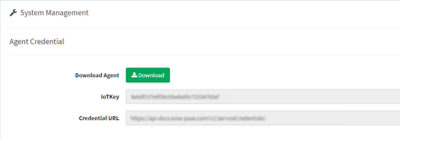
- Step 2-2: Click “Generate Agent Credential” botton to obtain IoTKey and Credential URL which will be needed when installing RMM EI Agent in Step 3 in order to connect agent to RMM cloud
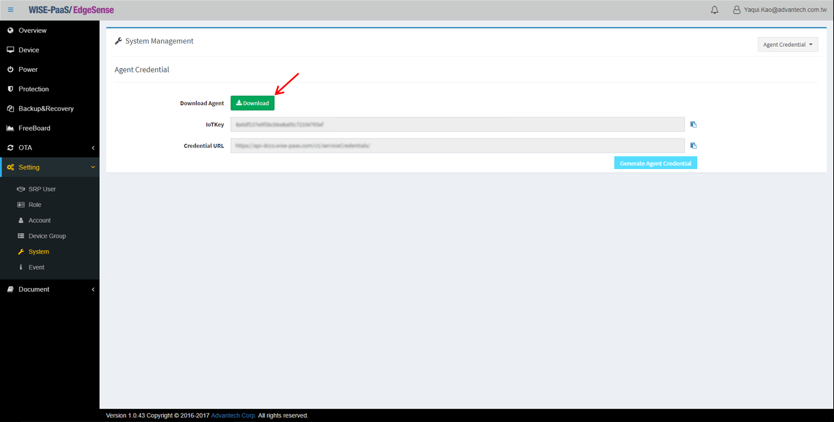
- Step 2-3: Click “Download” button to download RMM EI Agent instllation package
- Step 2-4: [Important Reminder] Please note that this step MUST BE taken on your edge devices
Execute RMM EI AgentSetep_1.0.9.exe file to start instllation process on agent devices
Step 3: Install RMM EI Agent
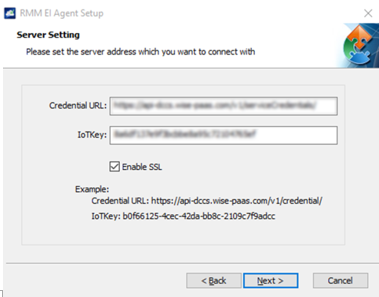
Enter Credential URL and IoTKey obtained earlier in EdgeSense management console (Step 2-2)
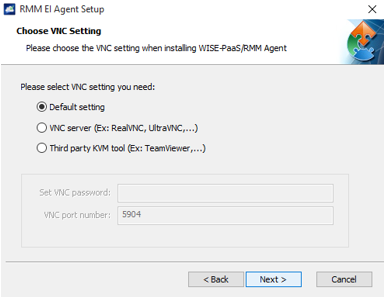
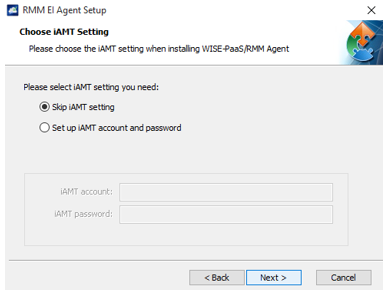
If your devices support iAMT, you can also enter your iAMT account and password here
(Note: iAMT may need to be enabled in BIOS first and MEBx configurations might as well needed)
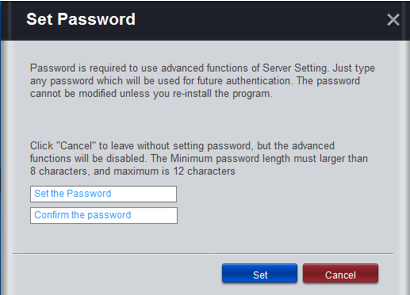
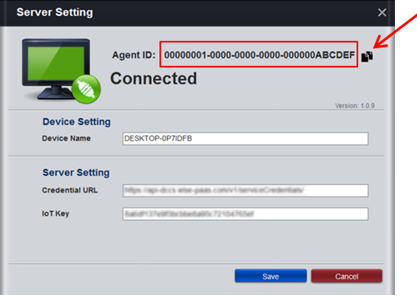
Launch “ServerSetting” under C:\Program Files (x86)\Advantech\RMM EI Agent (default folder)
You can set your password for accessing “ServerSetting”
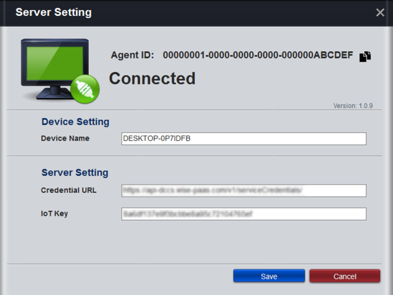
After setting password, please make sure it shows “Connected”, otherwise devices couldn’t get connected to RMM cloud
Step 4: Get Edge Devices Connected to RMM Cloud
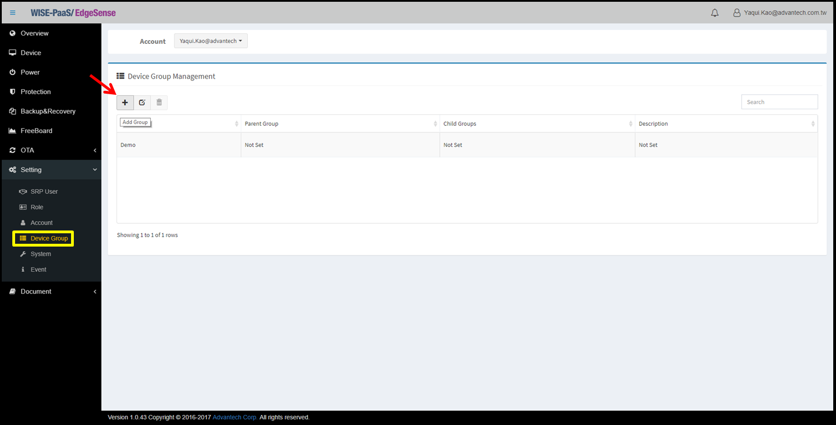
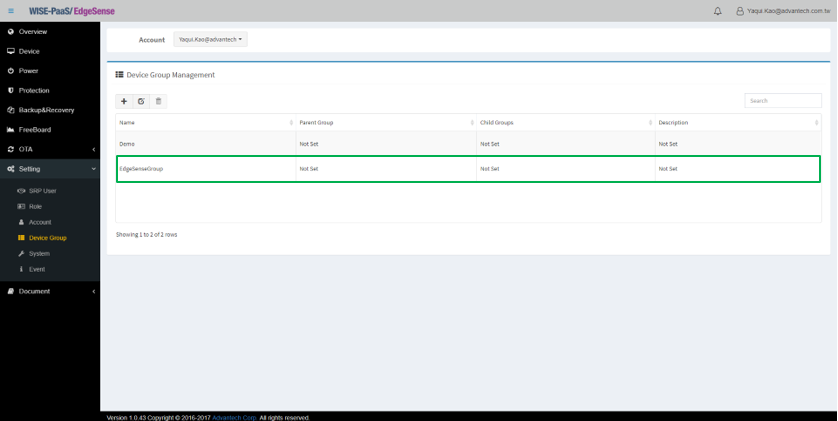
- Step 4-1: In management console, go to “Device Group” under “Setting” tab, then click “+” icon to add new group(s) before adding devices (Note: Please be noted that you HAVE TO create a new group before adding or assigning edge devices if there’s no existing group(s))
- Step 4-2: Enter the name and description (optional) of the group you’re creating
- Step 4-3: A notification window will pop up indicating your group has been created successfully
- Step 4-4: Now we can see a new group has been generated (EdgeSenseGroup here for example)
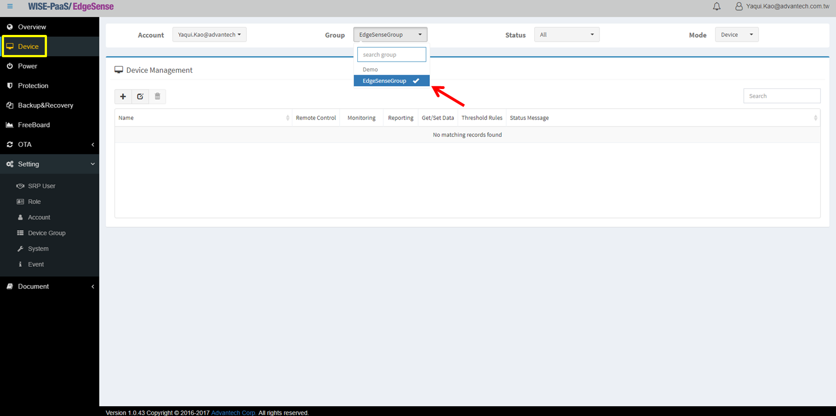
- Step 4-5: Go to “Device” tab on the left console, click drop-down list and select the group you want your edge devices to be assigned
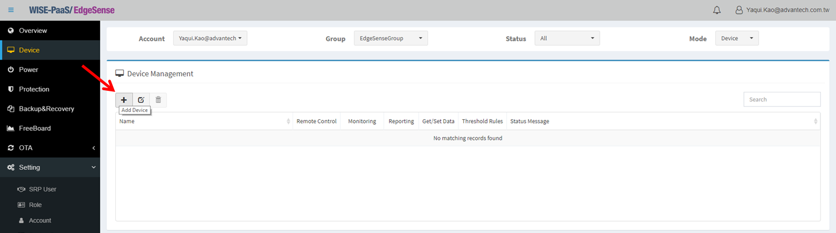
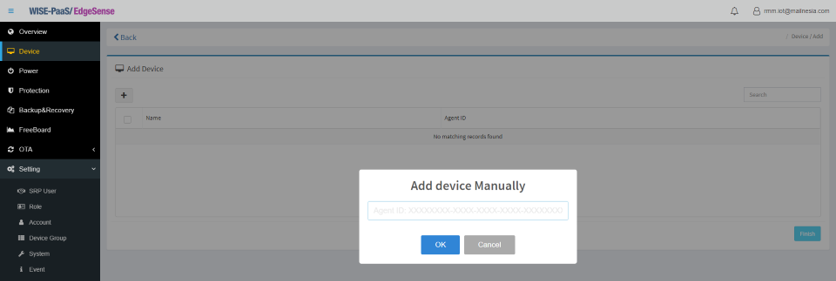
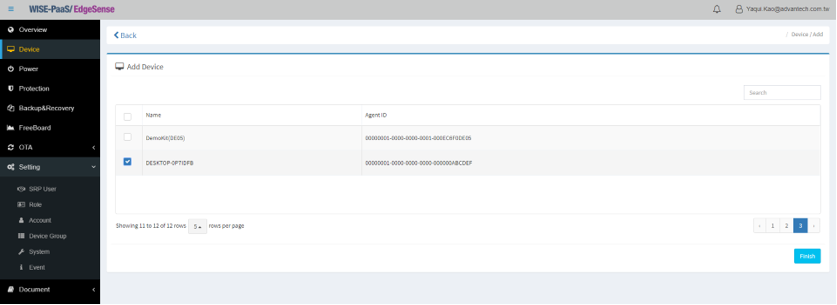
- Step 4-6: Click “+” icon to add device
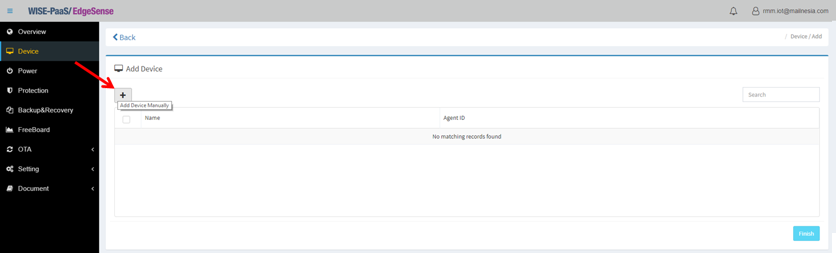
- Step 4-7: Then Click “+” icon to add device manually
- Step 4-8: Upon seeing this message box, go back and open ServerSetting (Step 3) on edge device then click the copy icon (as pointed in below screenshot) to copy full string of Agent ID
- Step 4-9: Paste the full string of Agent ID just copied in the blank
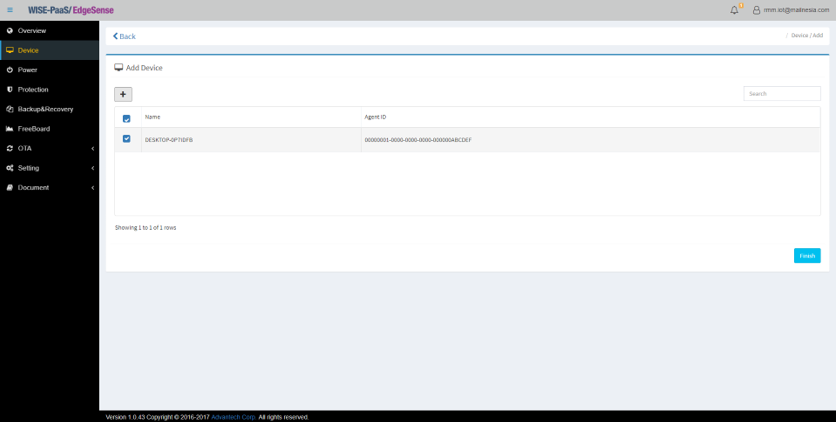
- Step 4-10: Edge device to be added/connected will then appear with its “Name” and “Agent ID”
- Step 4-11: Notification window will pop out indicating device(s) has been added to your group
- [Note] Generally if your account is signed up/created through WISE-PaaS/EdgeSense portal, default account role assigned is “device admin”. If you wish to have elavated priviledge/permission as “admin” which allows you to search all unassigned devices and decide which to add, please contact Advantech for more information
With “admin” permission, a list of unassigned devices will appear for users to search/select from
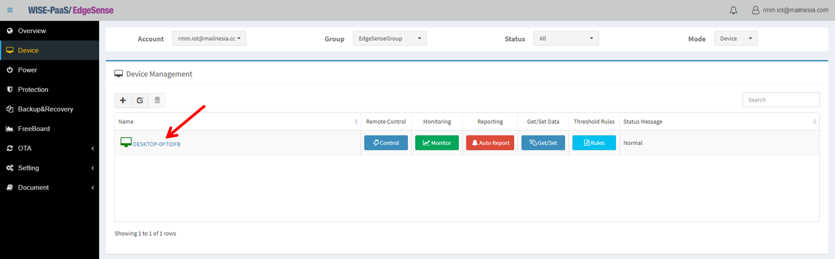
- Step 4-12: Now you should be able to see your connected devices in management console
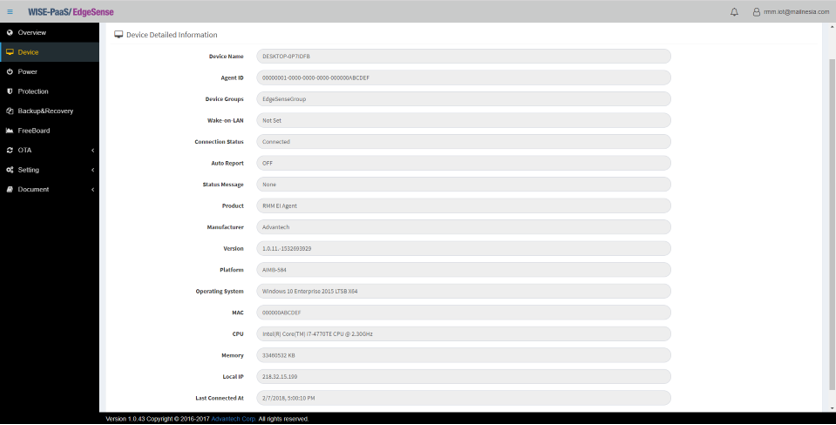
- Step 4-13: Click the name of the edge device you will see all detailed information of this device
Azure
Create Azure IoT Hub
To utilize Azure services, we need a Microsoft account to log in to azure portal. Following steps will create an azure iot hub to communicate with Advantech protocol connector modules.
Step 1. Log in to Microsoft Azure Portal
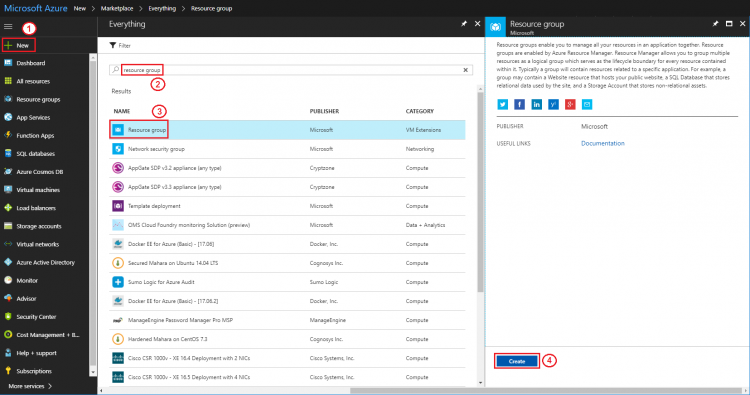
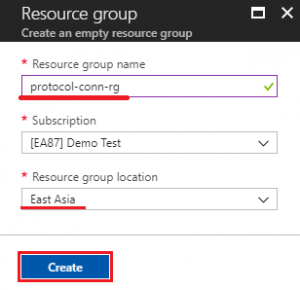
Step 2. Create a resource group
- Search “resource group” and create new one
- Input resource group name: protocol-conn-rg (for example)
- Select a location (service region): East Asia (for example)
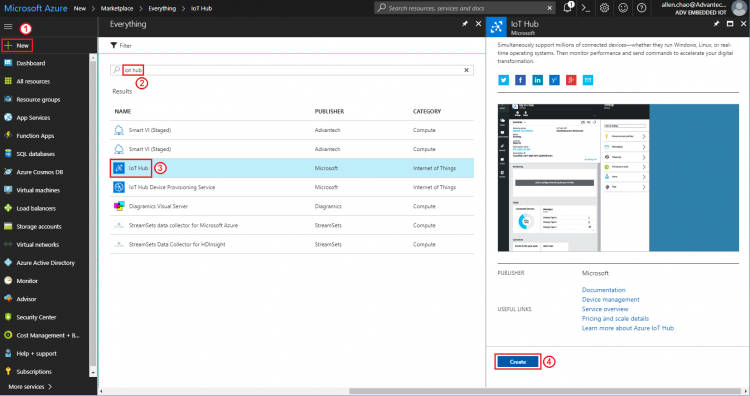
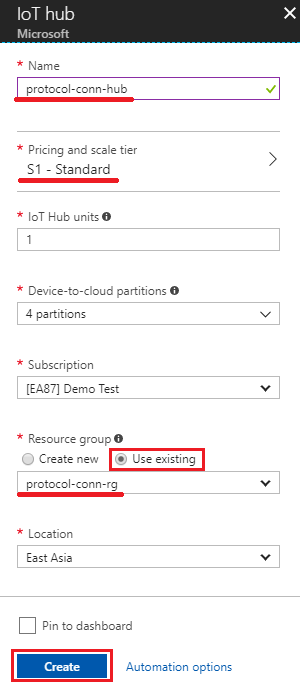
Step 3. Create an azure iot hub
- Search “iot hub” and create new one
- Input IoT hub name: protocol-conn-hub (for example)
- Select pricing and scale tier: here we chose “S1 - Standard”
- Select Resource group created at step 2: click “Use existing” and select “protocol-conn-rg”
Protocol Connector Using Node-RED
Cloud Environment Setups
Following steps will create an azure iot device to connect to iot hub created at previous section.
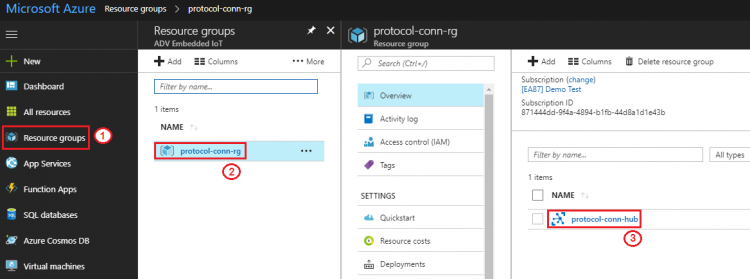
Step 1. Go to iot hub created at previous section: Resource groups → protocol-conn-rg → protocol-conn-hub
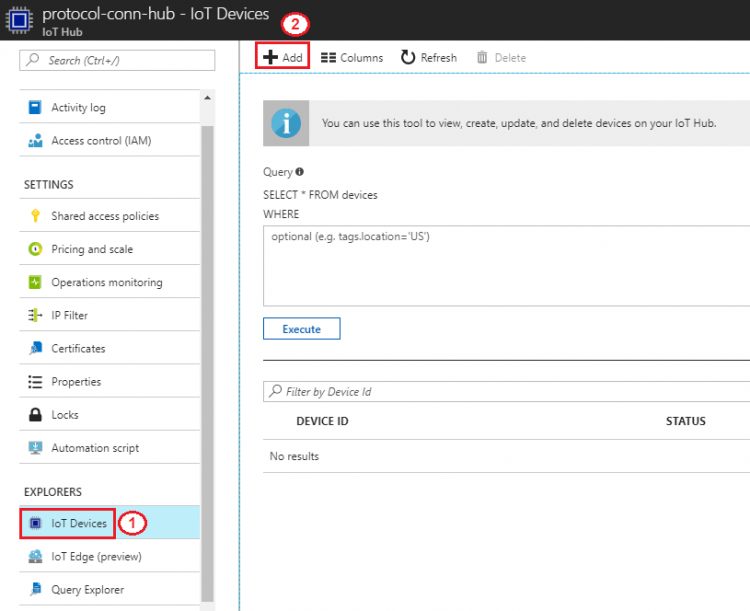
Step 2. IoT Devices → Add
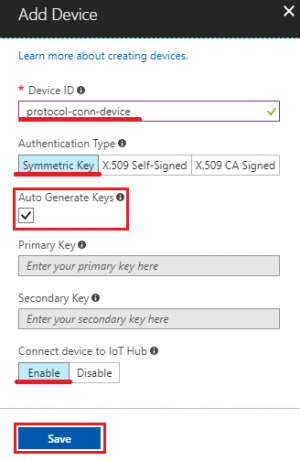
- Device ID: protocol-conn-device (for example)
- Authentication Type: select “Symmetric Key” for this tutorial
- Check “Auto Generate Keys”
- Connect device to IoT Hub: select “Enable”
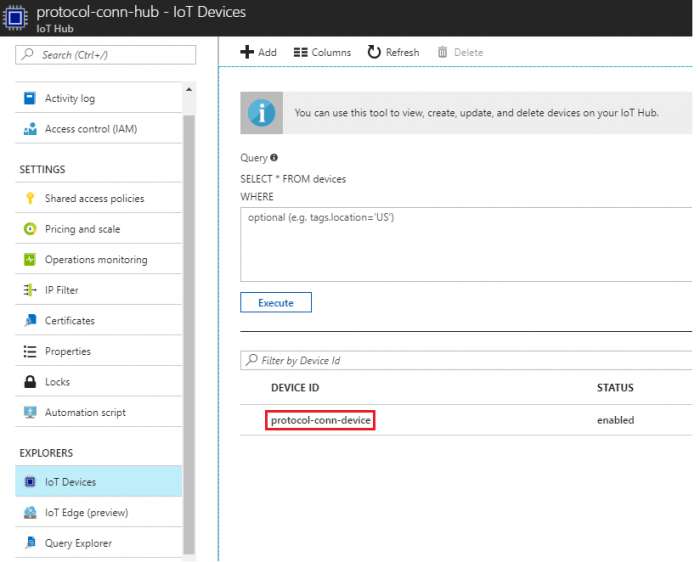
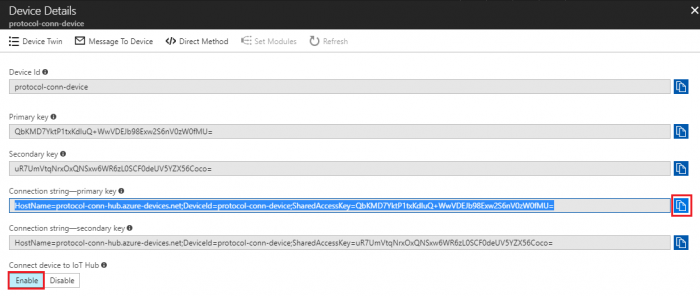
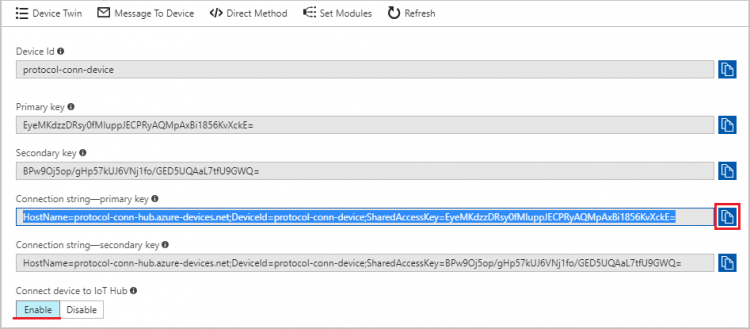
- Select the created iot device to get device connection string
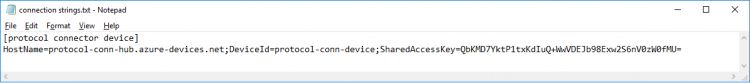
- Click
 to copy “Connection string-primary key” and make sure the "Connect device to IoT Hub" is "Enable"
to copy “Connection string-primary key” and make sure the "Connect device to IoT Hub" is "Enable"
- Save the connection string in a text file for later use
Device Environment Setups
Following steps will configure device Node-RED nodes to enable communications between Advantech protocol connector modules and azure iot hub.
Step 1. Open Node-RED page in the web browser (default URI is http://127.0.0.1:1880)
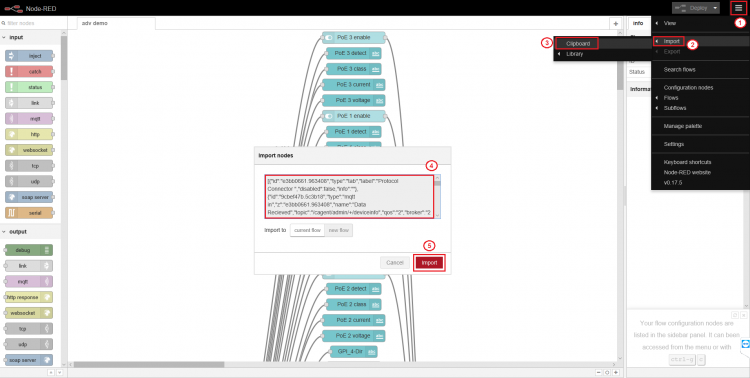
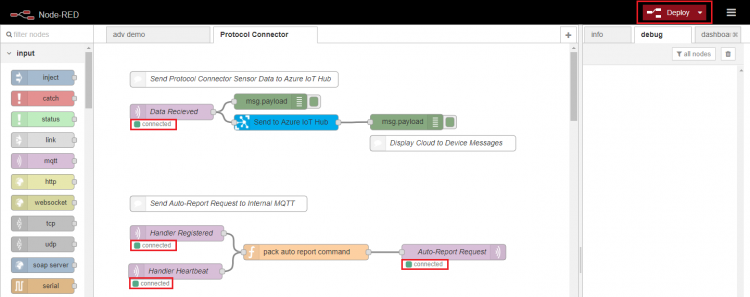
Step 2. Copy following content and import it into Node-RED
[
{"id": "ce169f53.786dd" , "type": "tab", "label": "Protocol Connector ", "disabled": false, "info": ""},
{"id": "104120.85f37ee" , "type": "mqtt in", "z": "ce169f53.786dd", "name": "Data Recieved", "topic": "/cagent/admin/+/deviceinfo", "qos": "2", "broker": "23acb8c5.a15ad8", "x": 150, "y": 132, "wires": [["12642914.e549c7", "95d1843d.e8a5c8"]]},
{"id": "97d0f87d.614ea8", "type": "mqtt out", "z": "ce169f53.786dd", "name": "Auto-Report Request", "topic": "", "qos": "0", "retain": "false", "broker": "23acb8c5.a15ad8", "x": 692.0001220703125, "y": 401, "wires": []},
{"id": "12642914.e549c7", "type": "debug", "z": "ce169f53.786dd", "name": "", "active": true, "console": "false", "complete": "payload", "x": 340, "y": 112, "wires": []},
{"id": "6bacc623.4bc318", "type": "comment", "z": "ce169f53.786dd", "name": "Send Protocol Connector Sensor Data to Azure IoT Hub", "info": "", "x": 270, "y": 69.36331176757812, "wires": []},
{"id": "4a9698eb.3deed8", "type": "comment", "z": "ce169f53.786dd", "name": "Send Auto-Report Request to Internal MQTT", "info": "", "x": 240, "y": 296, "wires": []},
{"id": "3a7f0c9.34066f4", "type": "mqtt in", "z": "ce169f53.786dd", "name": "Handler Registered", "topic": "/cagent/admin/+/agentinfoack", "qos": "2", "broker": "23acb8c5.a15ad8", "x": 160, "y": 364.8398742675781, "wires": [["3cd5a503.a6b2ca"]]},
{"id": "3cd5a503.a6b2ca", "type": "function", "z": "ce169f53.786dd", "name": "pack auto report command", "func": "var auto_rpt_msg = function(device) {\n return {\n topic: \"/cagent/admin/\" + device + \"/agentcallbackreq\",\n payload: {\n \"susiCommData\": {\n \"commCmd\": 2053,\n \"requestItems\": {\"All\":{}},\n \"autoUploadIntervalSec\": 10,\n \"handlerName\": \"general\"\n }\n }\n };\n};\n\nvar registered = context.get(\"registered\") || [];\nvar dev_id = msg.topic.replace(/^\\/cagent\\/admin\\/|\\/agentinfoack$|\\/notify$/g, \"\");\nvar is_reg_msg = (\n msg.topic.endsWith(\"agentinfoack\") && JSON.parse(msg.payload).susiCommData.status\n);\nvar msg_out = (is_reg_msg || (!~registered.indexOf(dev_id)))? auto_rpt_msg(dev_id) : null;\n\nif(!~registered.indexOf(dev_id)) {\n registered.push(dev_id);\n}\n\ncontext.set(\"registered\", registered);\nreturn msg_out;\n", "outputs": 1, "noerr": 0, "x": 418.0195617675781, "y": 401.00390625, "wires": [["97d0f87d.614ea8"]]},
{"id": "95d1843d.e8a5c8", "type": "azureiothub", "z": "ce169f53.786dd", "name": "Send to Azure IoT Hub", "protocol": "http", "x": 370, "y": 152, "wires": [["ecc11415.86a138"]]},
{"id": "ecc11415.86a138", "type": "debug", "z": "ce169f53.786dd", "name": "", "active": true, "console": "false", "complete": "payload", "x": 601.5, "y": 151.29998779296875, "wires": []},
{"id": "bf50c923.03a288", "type": "comment", "z": "ce169f53.786dd", "name": "Display Cloud to Device Messages", "info": "", "x": 671, "y": 192, "wires": []},
{"id": "71829e36.9c78c" , "type": "mqtt in", "z": "ce169f53.786dd", "name": "Handler Heartbeat", "topic": "/cagent/admin/+/notify", "qos": "2", "broker": "23acb8c5.a15ad8", "x": 157, "y": 438, "wires": [["3cd5a503.a6b2ca"]]},
{"id": "23acb8c5.a15ad8", "type": "mqtt-broker", "z": "", "broker": "127.0.0.1", "port": "1883", "clientid": "", "usetls": false, "compatmode": true, "keepalive": "60", "cleansession": true, "willTopic": "", "willQos": "0", "willPayload": "", "birthTopic": "", "birthQos": "0", "birthPayload": ""}
]
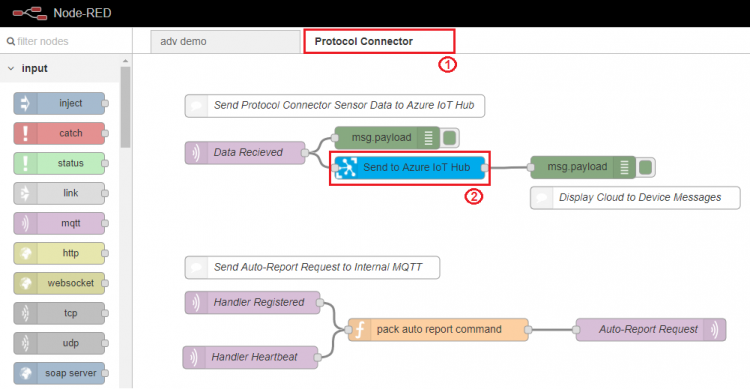
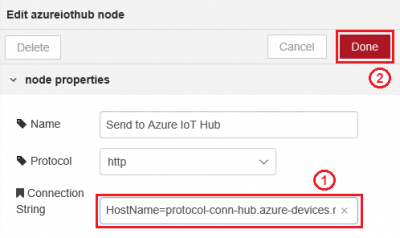
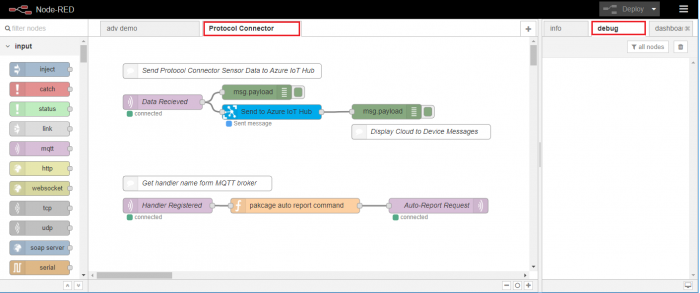
Step 3. Select "Protocol Connector" tab and double click "Send to Azure IoT Hub" node to configure node settings.
Step 4. Copy the saved device connection string and paste to "Connection String" field
Step 5. Click ![]() to complete edge device environment setups and make sure the states of MQTT nodes are "connected"
to complete edge device environment setups and make sure the states of MQTT nodes are "connected"
Protocol Connector Using IoT Edge
Prerequisites
Before to perform Azure IoT Edge environment setup steps, please make sure all following packages and tools are available and are correctly setup.
Windows Host
- Docker:
- Python:
2. Make sure the “pip” command is available.
- IoT Edge Runtime Control Tool:
1. Install IoT Edge control script (may need to run as administrator)
pip install -U azure-iot-edge-runtime-ctl2. Make sure the “iotedgectl” command is available. (the version number may be different)
Linux Host
- Docker:
1. Install Docker and check "docker" command is available. (the version number may be different).
- Python pip:
1. Install Python pip command.
sudo apt-get install python-pip
2. Make sure the “pip” command is available.
- IoT Edge Runtime Control Tool:
1. Install IoT Edge control script (may need to run as root)
pip install -U azure-iot-edge-runtime-ctl
2. Make sure the “iotedgectl” command is available. (the version number may be different)
Cloud Environment Setups
Following steps will create an azure iot edge device at previously created iot hub.
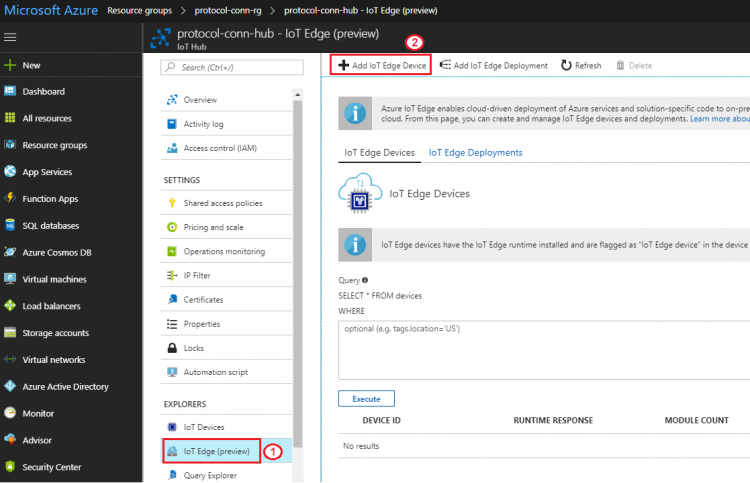
Step 1. Create an iot edge device
- Go to iot hub created at previous section: Resource groups → protocol-conn-rg → protocol-conn-hub
- IoT Edge → Add IoT Edge Device
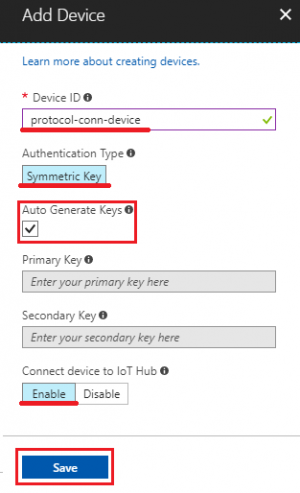
- Device ID: protocol-conn-device (for example)
- Authentication Type: select “Symmetric Key” for this tutorial
- Check “Auto Generate Keys”
- Connect device to IoT Hub: select “Enable”
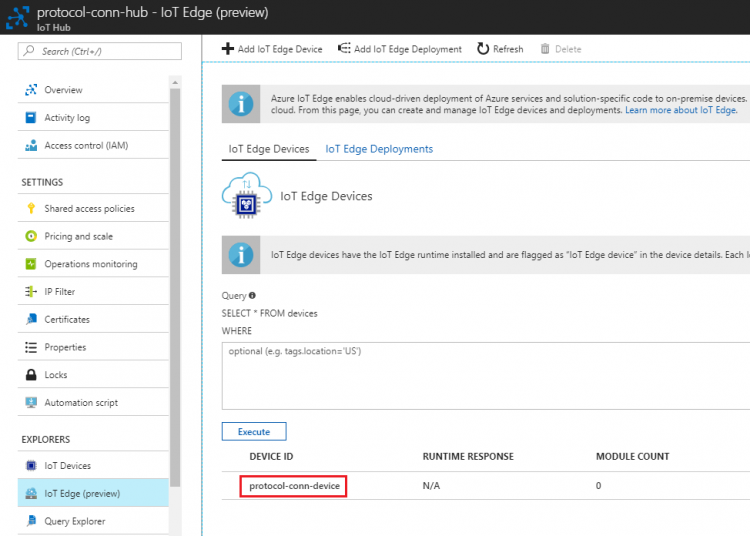
- Select the created iot edge device to get device connection string
- Click
 to copy “Connection string-primary key” and make sure the "Connect device to IoT Hub" is "Enable"
to copy “Connection string-primary key” and make sure the "Connect device to IoT Hub" is "Enable"
- Save the connection string in a text file for later use
Device Environment Setups
Following steps will configure edge device to bind to azure iot edge device previously created.
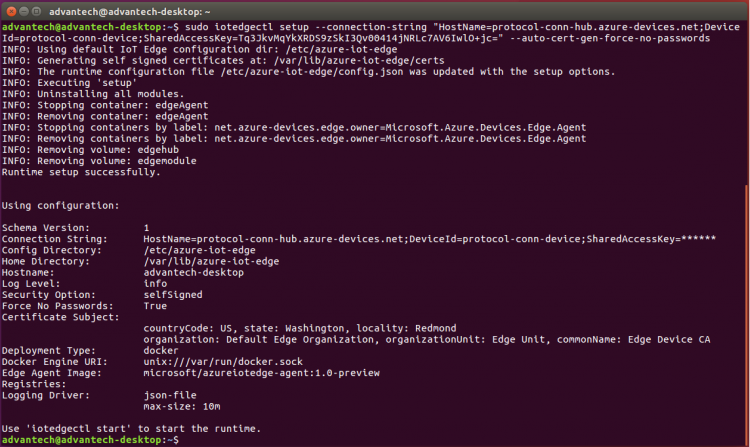
Step 1. Configure the iot edge runtime (need administrator privileges on windows 10 host or root privileges on linux host)
- Open a command prompt and type following command. Replace "{your iot edge device connection string}" with the saved device connection string
iotedgectl setup --connection-string "{your iot edge device connection string}" --auto-cert-gen-force-no-passwords
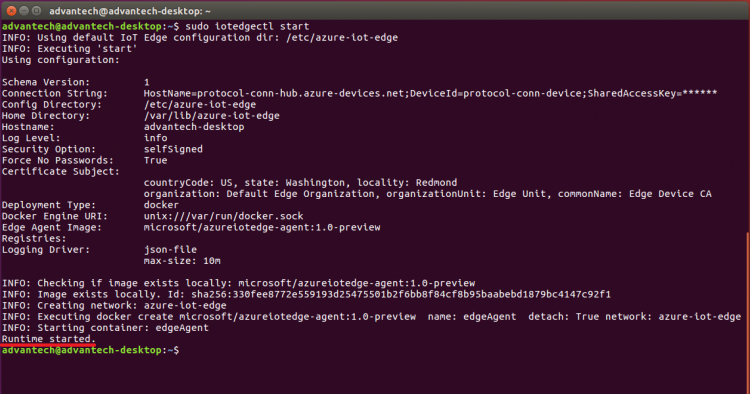
- Start the IoT Edge runtime
iotedgectl start
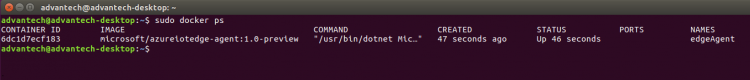
- Check Docker to see that the IoT Edge agent is running as a module
docker ps
Deploy an iot edge device module to edge device
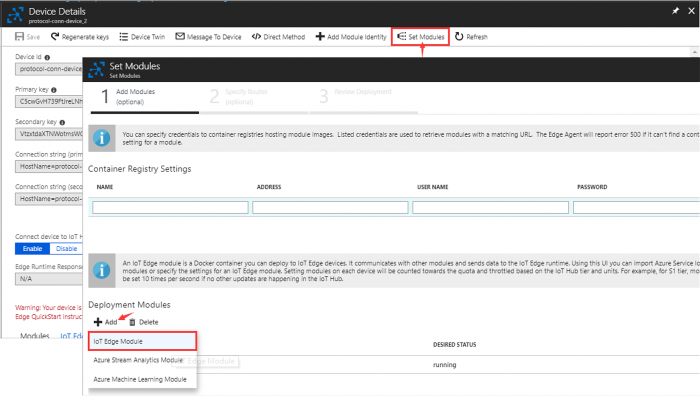
Step 1. Select iot edge device created at previous section
Step 2. Set Modules → Add IoT Edge Module
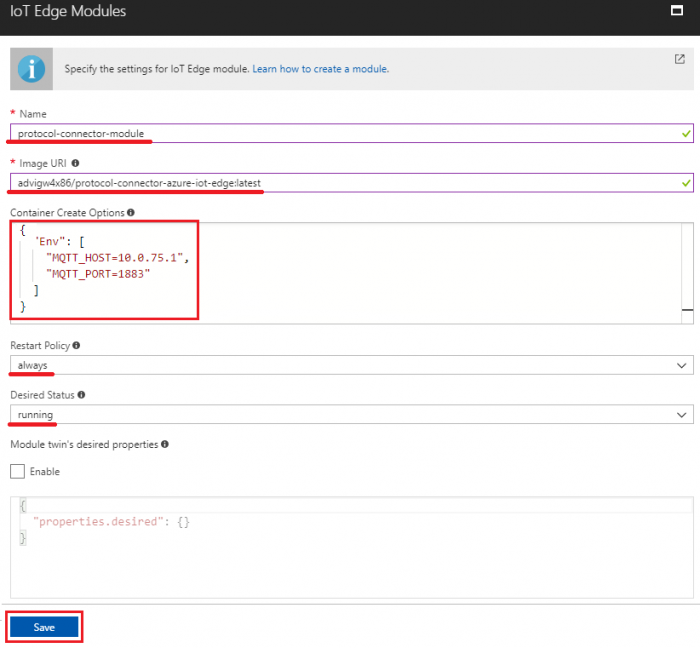
- Name: protocol-connector-module
- Image URI: advigw4x86/protocol-connector-azure-iot-edge:latest
- Container Create Options:
- In Windows host, paste following content
{
"Env": ["MQTT_HOST=10.0.75.1", "MQTT_PORT=1883"]
}
- In Linux host, paste following content
{
"Env": ["MQTT_HOST=172.17.0.1", "MQTT_PORT=1883"]
}
- Restart Policy: select “always”
- Desired Status: select “running”
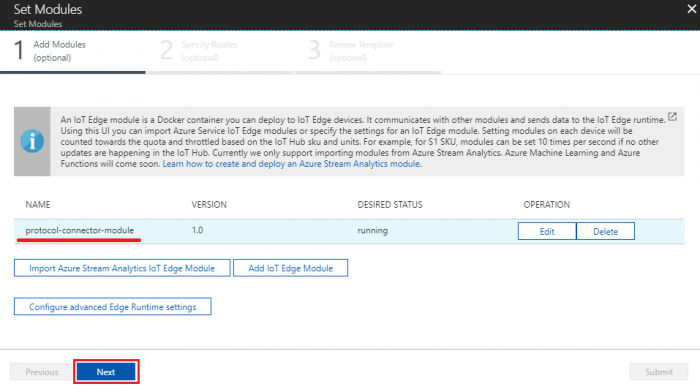
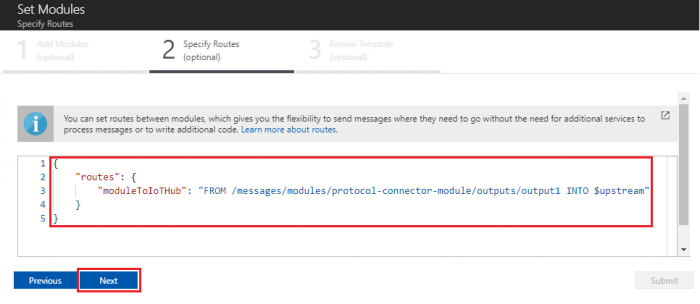
- Click “Next” to specify routes step
- Paste following content to specify route and click “Next” to review template
{
"routes": {
"moduleToIoTHub": "FROM /messages/modules/protocol-connector-module/outputs/output1 INTO $upstream"
}
}
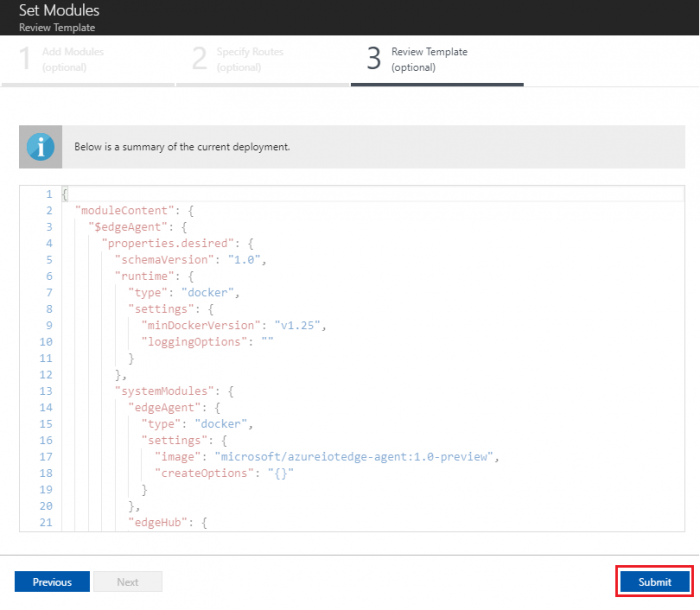
- In the Review Template step, click “Submit”
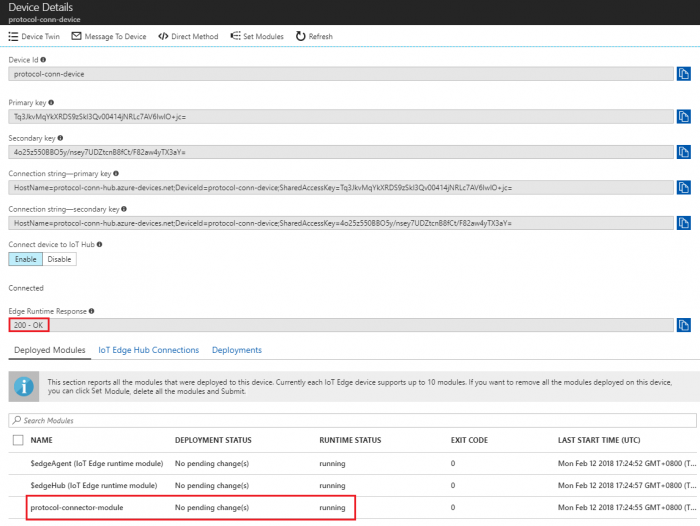
- Return to the IoT Edge device details page and click Refresh. The "protocol-connector-module" should be running along with the IoT Edge runtime
Monitor Messages
Device to Cloud (D2C)
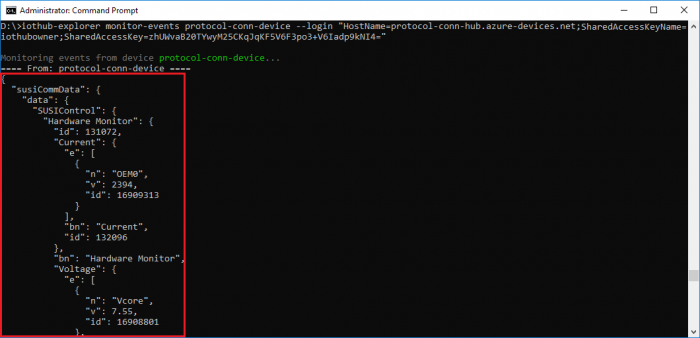
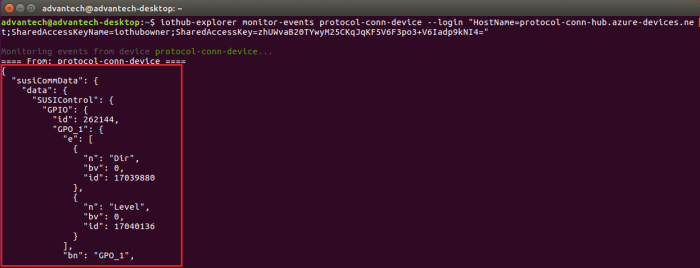
- use iothub-explorer tool (require nodejs and npm) to monitor D2C messages.
npm install -g iothub-explorer
iothub-explorer monitor-events iotedge-protocol-connector --login "{your iot hub connection string}"
Cloud to Device (C2D)
- C2D message is not yet ready on IoT Edge public preview.
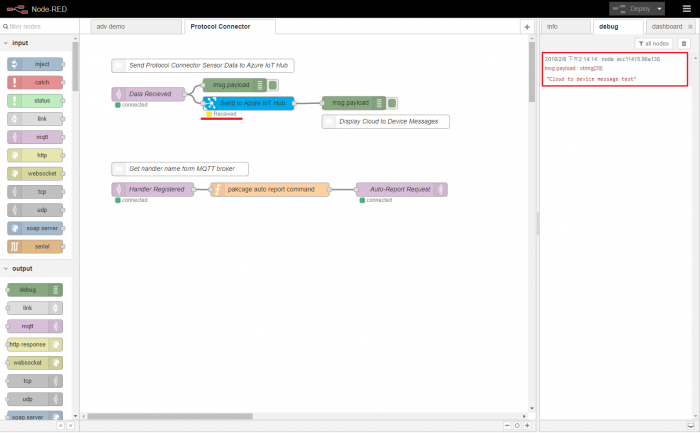
- For Node-RED protocol connector modules, we can take following steps to send C2D messages.
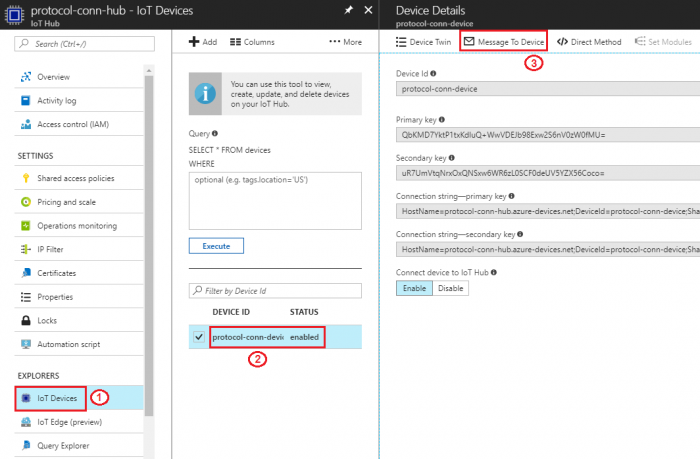
Step 1. Open Node-RED in web browser, select Protocol Connector and click the debug tab
Step 2. Go to iot device created at previous section: Resource groups → protocol-conn-rg → protocol-conn-hub → protocol-conn-device, then select "Message To Device"
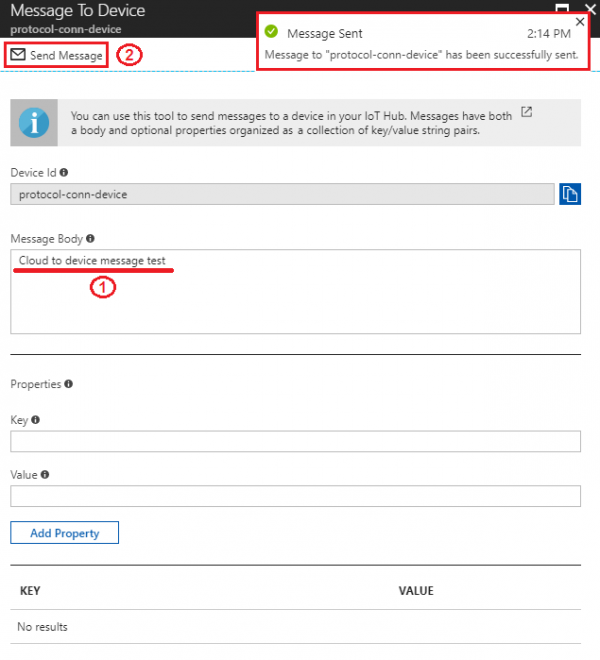
Step 3. Type our cloud to device messages in "Message Body" field then click "Send Message".
Step 4. Back to Node-RED page, we can see the received message
AWS
Node-Red
Prerequisites:
- AWS account
- this example use service which is region in US East (N. Virginia).
Cloud Environment Setups
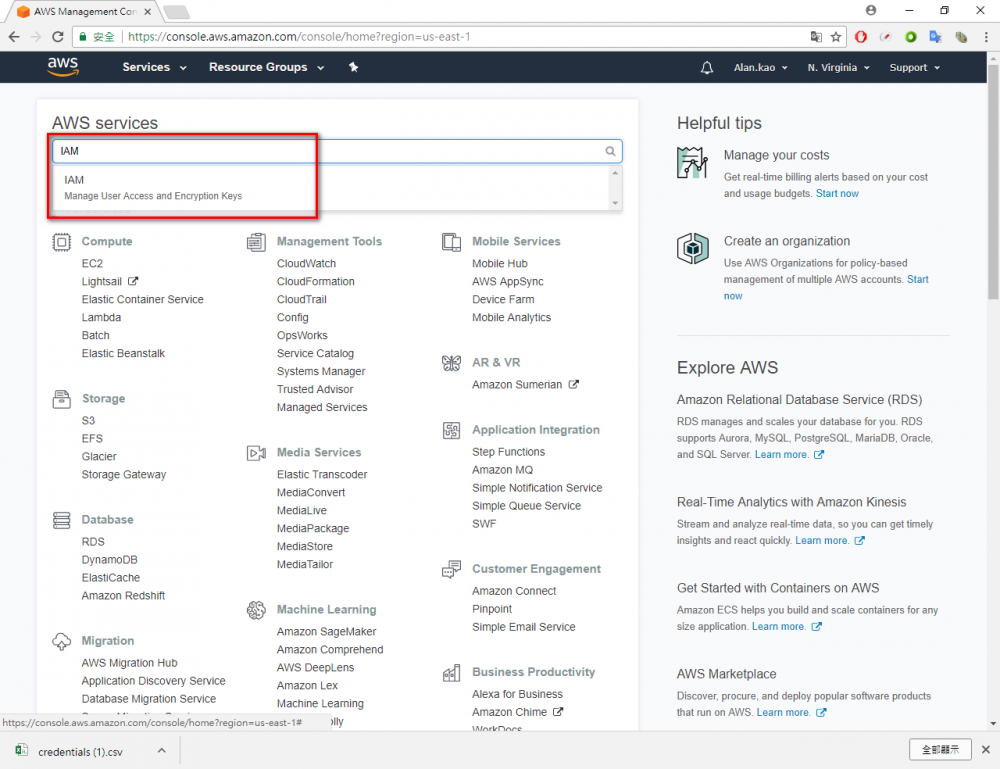
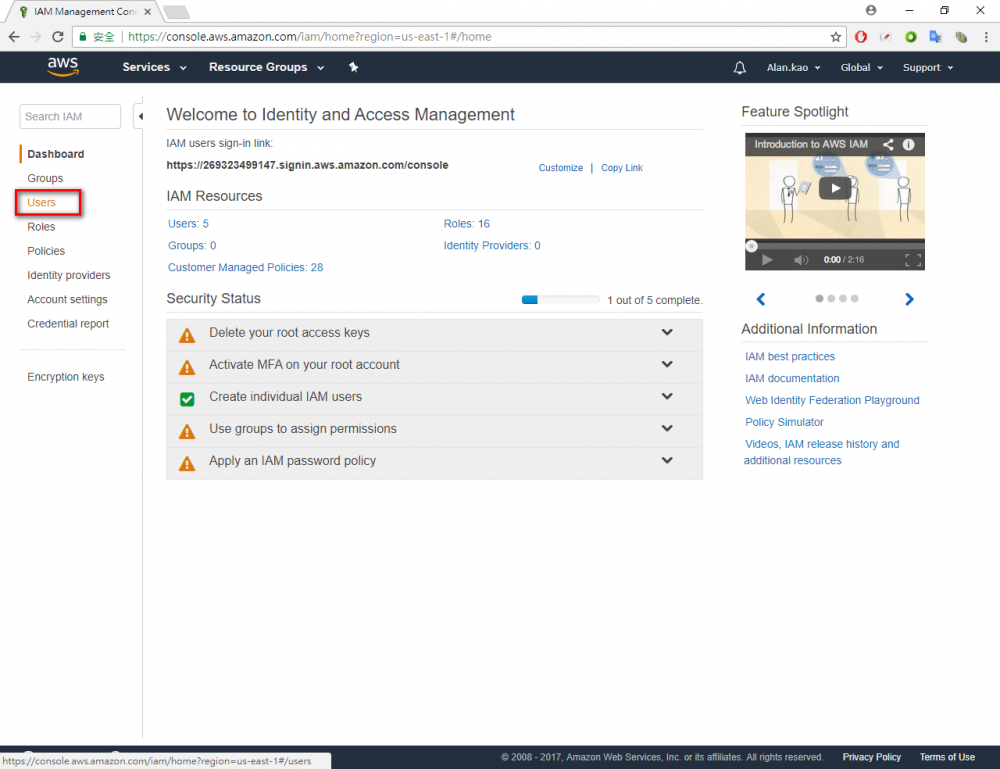
Step 1.Return the AWS console and go to IAM menu.
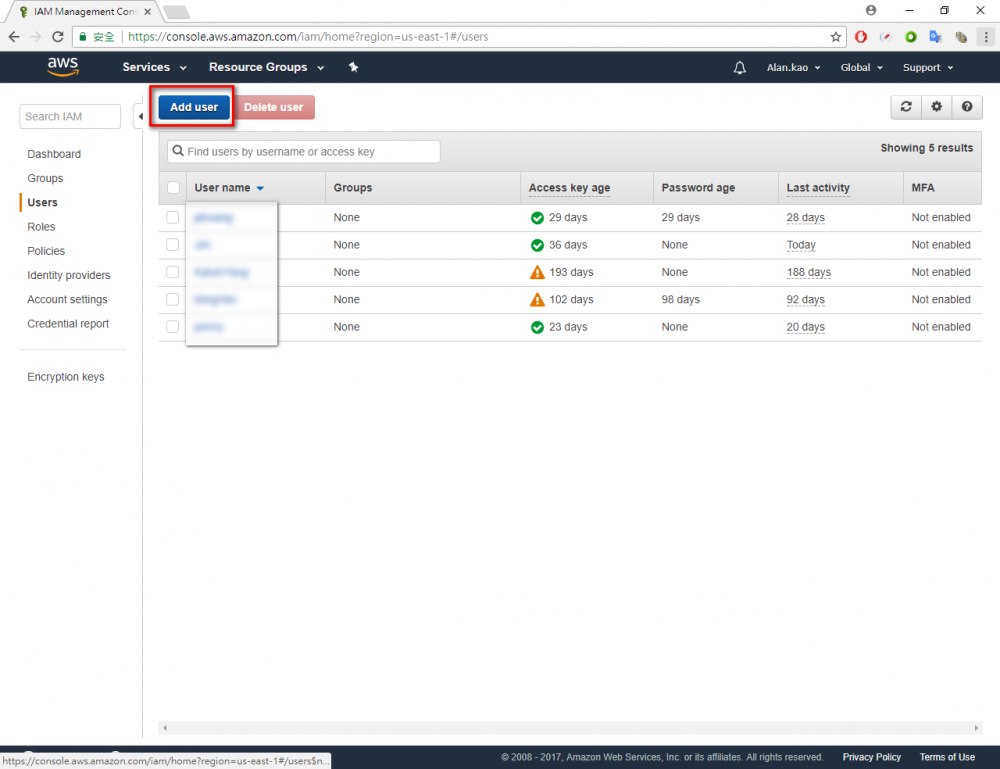
Step 2.Click “user” menu
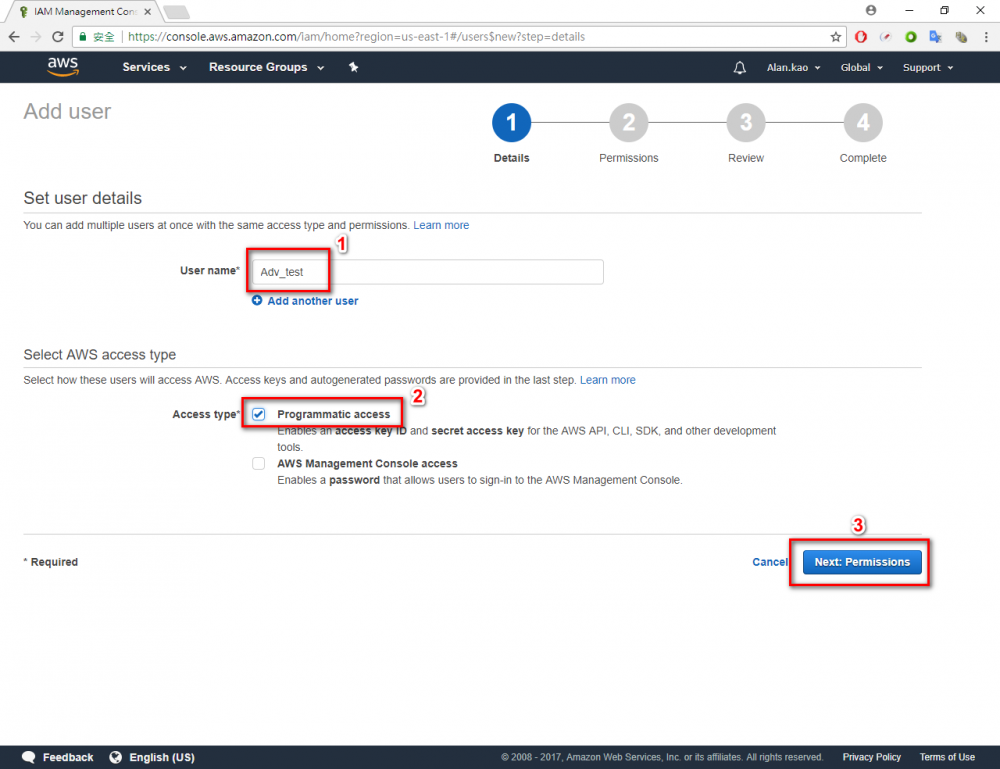
Step 3.Click “Add user” button
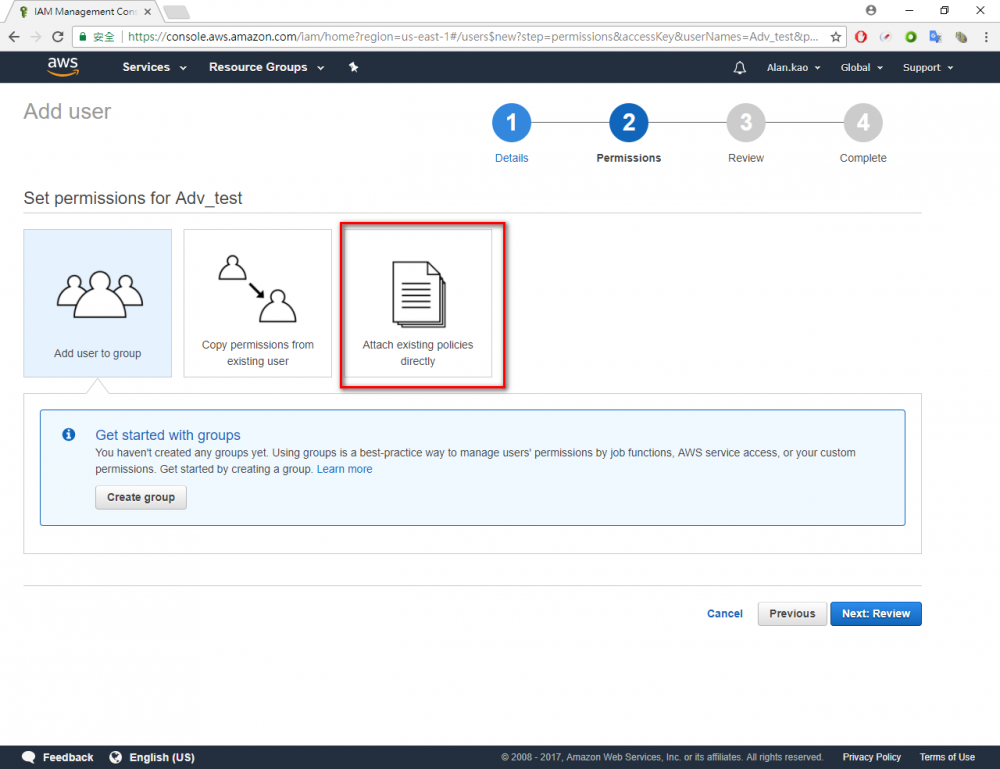
Step 4.Enter your user name. In this example user name is “Adv_test”.→ chose Programmatic access → Click “Next Permissions” button.
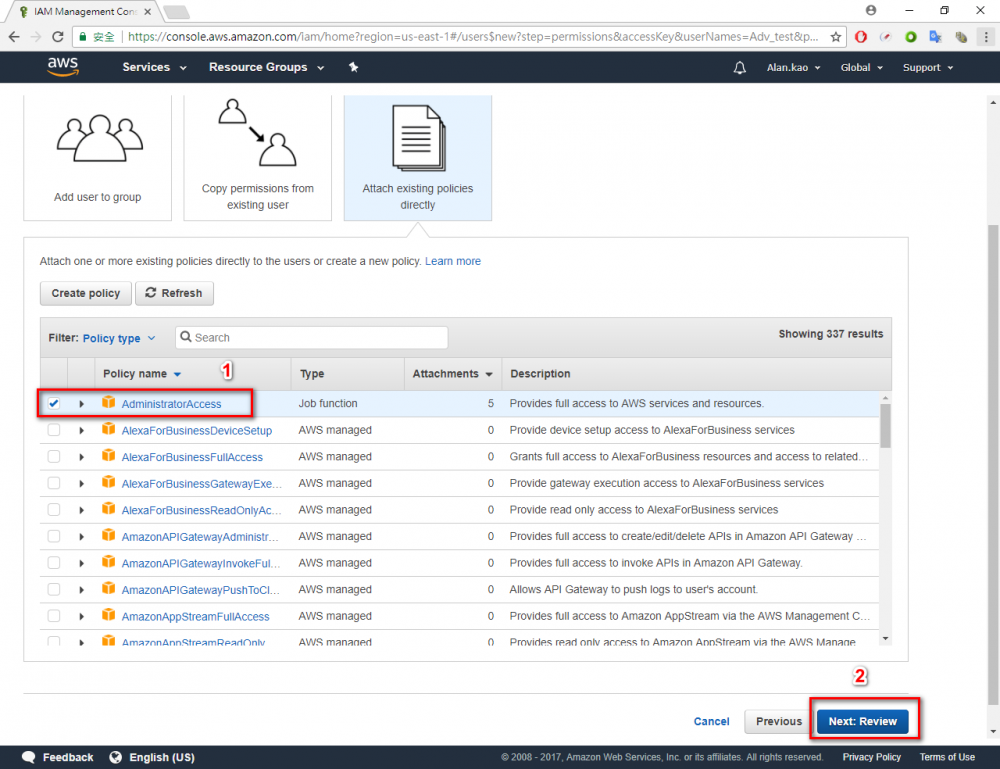
Step 6.Choose AdministratorAccess → Click “Next: Review” button
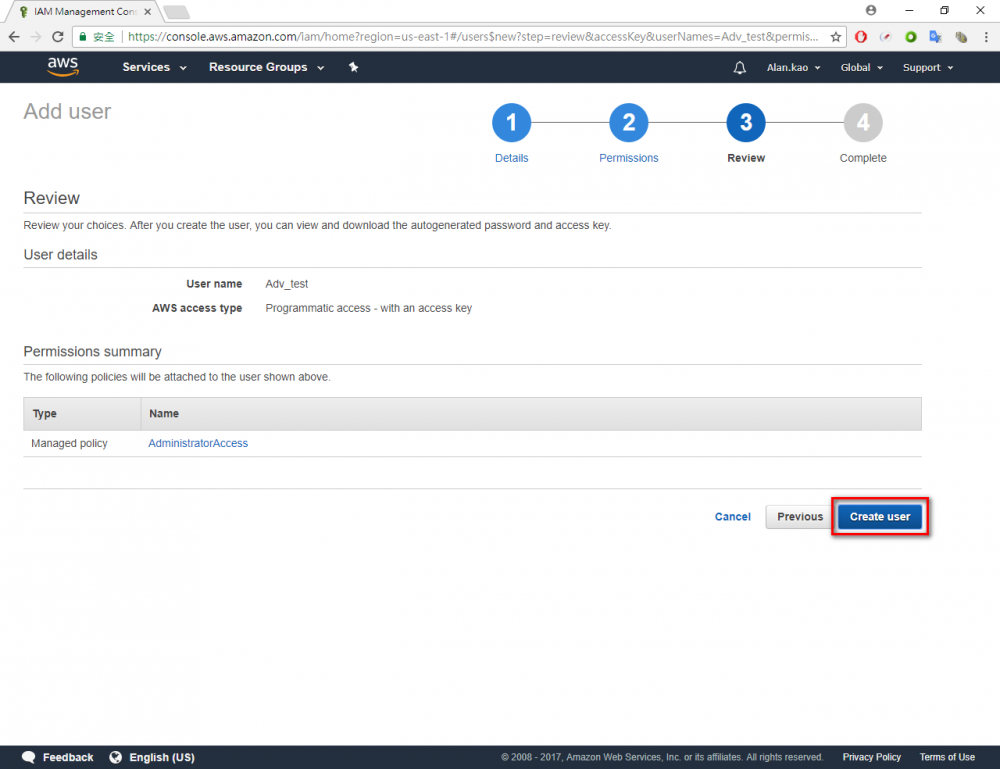
Step 7.Click “Create user”
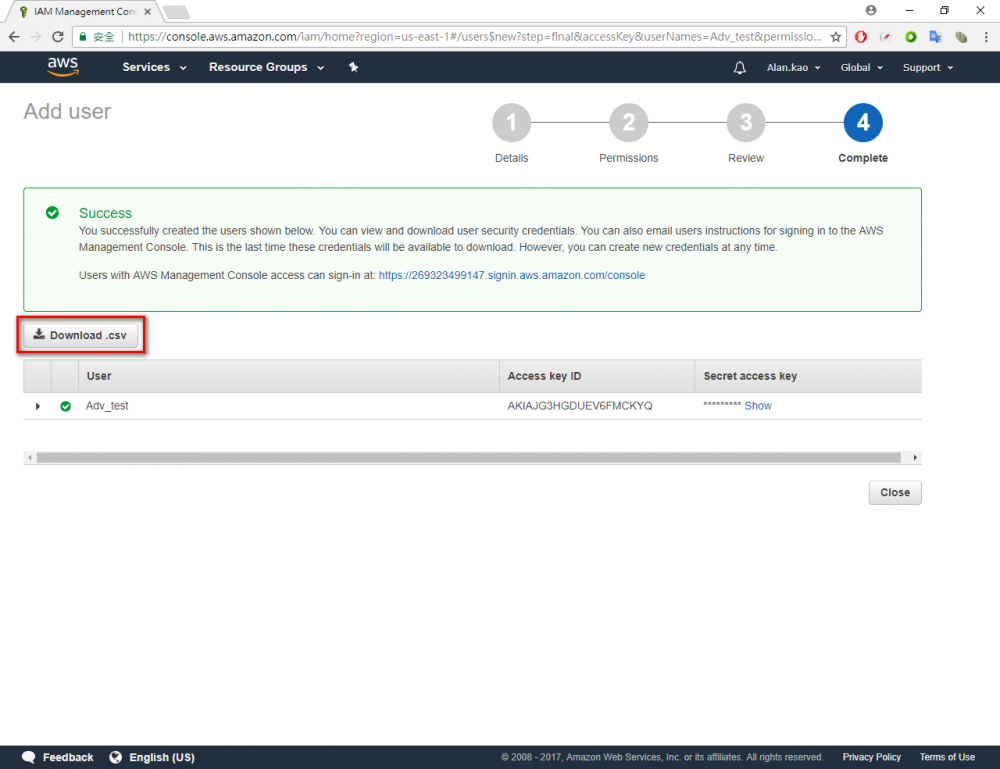
Step 8.Download the credentials. This is the last time these credentials will be available to download.
Step 9.Click “Download .csv” button
Device Environment Setups
In this section, you will install Advantech Node-Red tool for and Configurate the setting to connect AWS IoT
- click on desktop to open NodeRED in web browser
Set up edge device environment
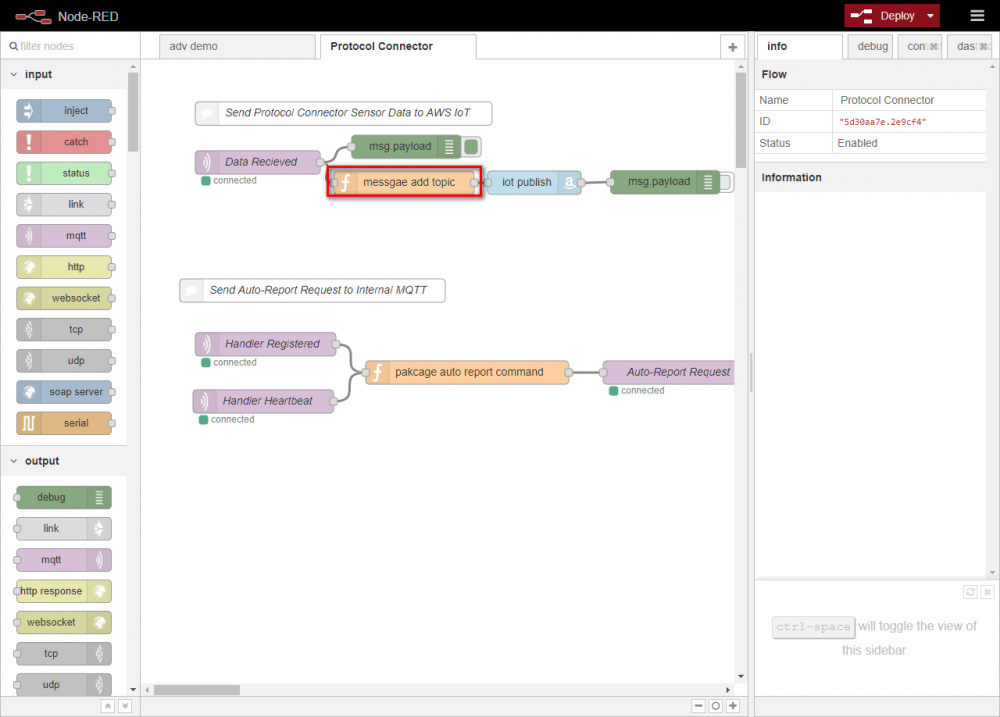
- Copy following NodeRED flow and import it into NodeRED:
[{"id":"d652f017.65e74","type":"tab","label":"Protocol Connector ","disabled":false,"info":""},
{"id":"bec4e2f6.b7b83","type":"mqtt in","z":"d652f017.65e74","name":"Data Recieved","topic":"/cagent/admin/+/deviceinfo","qos":"2","broker":"22aa981b.46a50c","x":150,"y":132,"wires":[["5651a33f.5722bc","cd4723c3.e1624"]]},{"id":"cd4723c3.e1624","type":"debug","z":"d652f017.65e74","name":"","active":true,"console":"false","complete":"payload","x":340,"y":112,"wires":[]},
{"id":"f7640bf7.c78ab8","type":"comment","z":"d652f017.65e74","name":"Send Protocol Connector Sensor Data to AWS IoT","info":"","x":260,"y":69.36331176757812,"wires":[]},
{"id":"f6c0c463.1d1928","type":"comment","z":"d652f017.65e74","name":"Send Auto-Report Request to Internal MQTT","info":"","x":220,"y":296,"wires":[]},
{"id":"5651a33f.5722bc","type":"function","z":"d652f017.65e74","name":"messgae topic","func":"var device_id = 'DK10';\nvar plugin_id = msg.topic.replace(/^\\/cagent\\/admin\\/|\\/deviceinfo$/g, \"\");\nmsg.topic = 'protocol-conn/' + device_id + '/' + plugin_id;\nreturn msg;","outputs":1,"noerr":0,"x":350,"y":157.10000610351562,"wires":[["bb0580c5.75a24"]]},{"id":"b74f9d97.3e912","type":"mqtt out","z":"d652f017.65e74","name":"Auto-Report Request","topic":"","qos":"0","retain":"false","broker":"22aa981b.46a50c","x":692.0001220703125,"y":401,"wires":[]},
{"id":"828deeb3.bd324","type":"mqtt in","z":"d652f017.65e74","name":"Handler Registered","topic":"/cagent/admin/+/agentinfoack","qos":"2","broker":"22aa981b.46a50c","x":160,"y":364.8398742675781,"wires":[["8e87ec7b.6487b"]]},
{"id":"8e87ec7b.6487b","type":"function","z":"d652f017.65e74","name":"pakcage auto report command","func":"var auto_rpt_msg = function(device) {\n return {\n topic: \"/cagent/admin/\" + device + \"/agentcallbackreq\",\n payload: {\n \"susiCommData\": {\n \"commCmd\": 2053,\n \"requestItems\": {\"All\":{}},\n \"autoUploadIntervalSec\": 10,\n \"handlerName\": \"general\"\n }\n }\n };\n};\n\nvar registered = context.get(\"registered\") || [];\nvar dev_id = msg.topic.replace(/^\\/cagent\\/admin\\/|\\/agentinfoack$|\\/notify$/g, \"\");\nvar is_reg_msg = (\n msg.topic.endsWith(\"agentinfoack\") && JSON.parse(msg.payload).susiCommData.status\n);\nvar msg_out = (is_reg_msg || (!~registered.indexOf(dev_id)))? auto_rpt_msg(dev_id) : null;\n\nif(!~registered.indexOf(dev_id)) {\n registered.push(dev_id);\n}\n\ncontext.set(\"registered\", registered);\nreturn msg_out;\n","outputs":1,"noerr":0,"x":418.0195617675781,"y":401.00390625,"wires":[["b74f9d97.3e912"]]},{"id":"b06132d0.4baf6","type":"mqtt in","z":"d652f017.65e74","name":"Handler Heartbeat","topic":"/cagent/admin/+/notify","qos":"2","broker":"22aa981b.46a50c","x":157,"y":438,"wires":[["8e87ec7b.6487b"]]},
{"id":"bb0580c5.75a24","type":"AWS IotData","z":"d652f017.65e74","aws":"20e9a430.34135","operation":"Publish","thingName":"","topic":"","payload":"","endPoint":"","name":"","x":535,"y":156.75,"wires":[[]]},{"id":"22aa981b.46a50c","type":"mqtt-broker","z":"","broker":"127.0.0.1","port":"1883","clientid":"","usetls":false,"compatmode":true,"keepalive":"60","cleansession":true,"willTopic":"","willQos":"0","willPayload":"","birthTopic":"","birthQos":"0","birthPayload":""},
{"id":"20e9a430.34135","type":"amazon config","z":"","name":"AWS","region":"us-east-1"}]
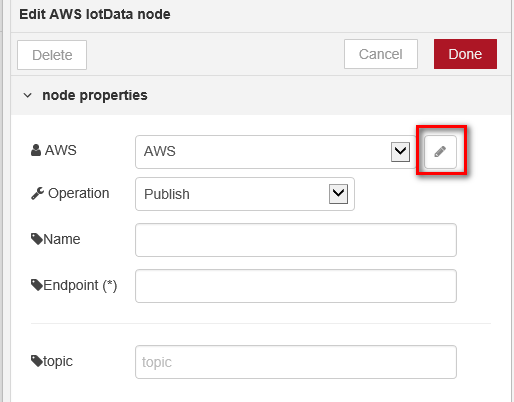
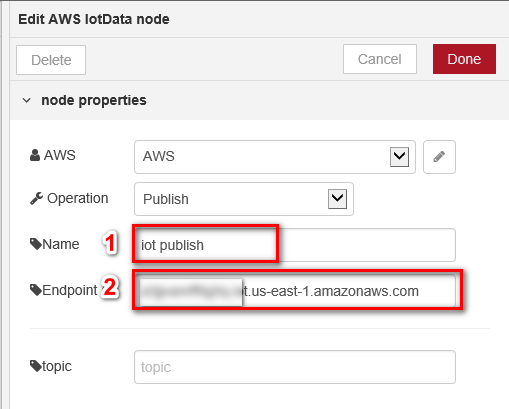
- Switch to Protocol Connector tab and double click “IotData Publish” node to set device configuration.
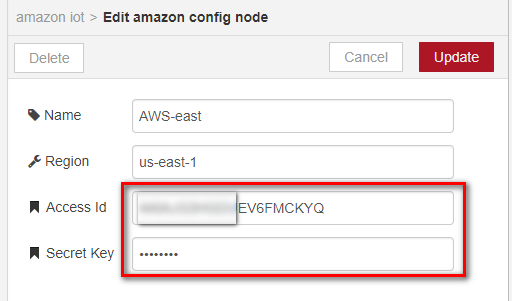
- Enter the Access Id and Secret Key which is on credentials .csv file.
- Enter the Name “IoT Pubilsh” and Endpoint
- You can find endpoint in AWS IoT console.
- Check your message topic on the "message topic' function node
- Enter {your devie id} in device_id, you can choose {your device id} which you want.
[[File:2018-02-13 152702.png|center|2018-02-13_152702.png]]
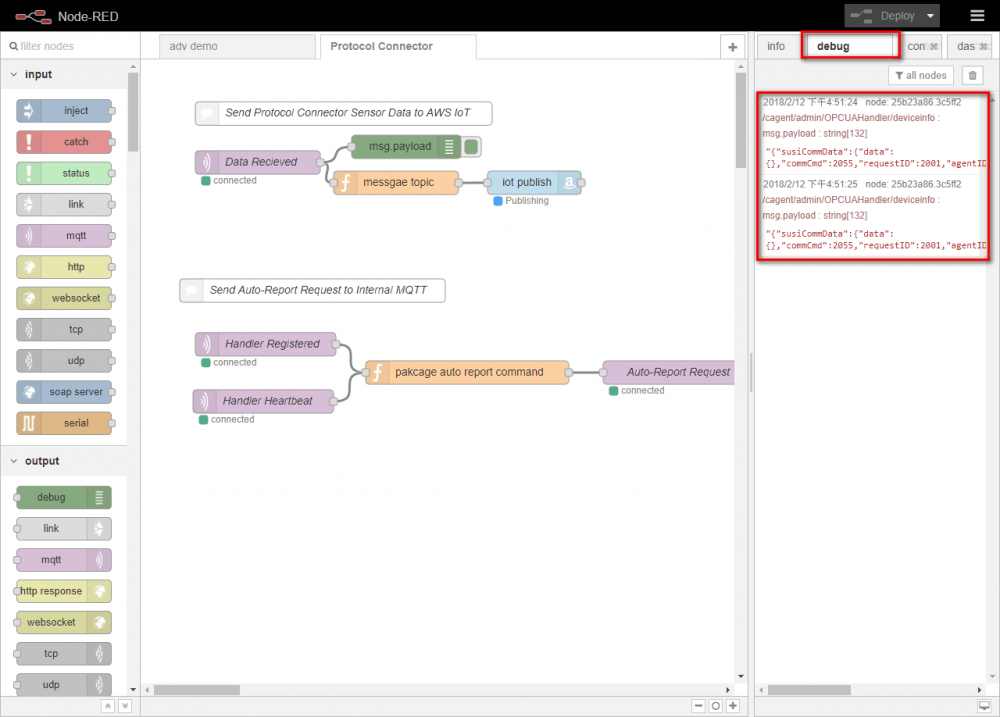
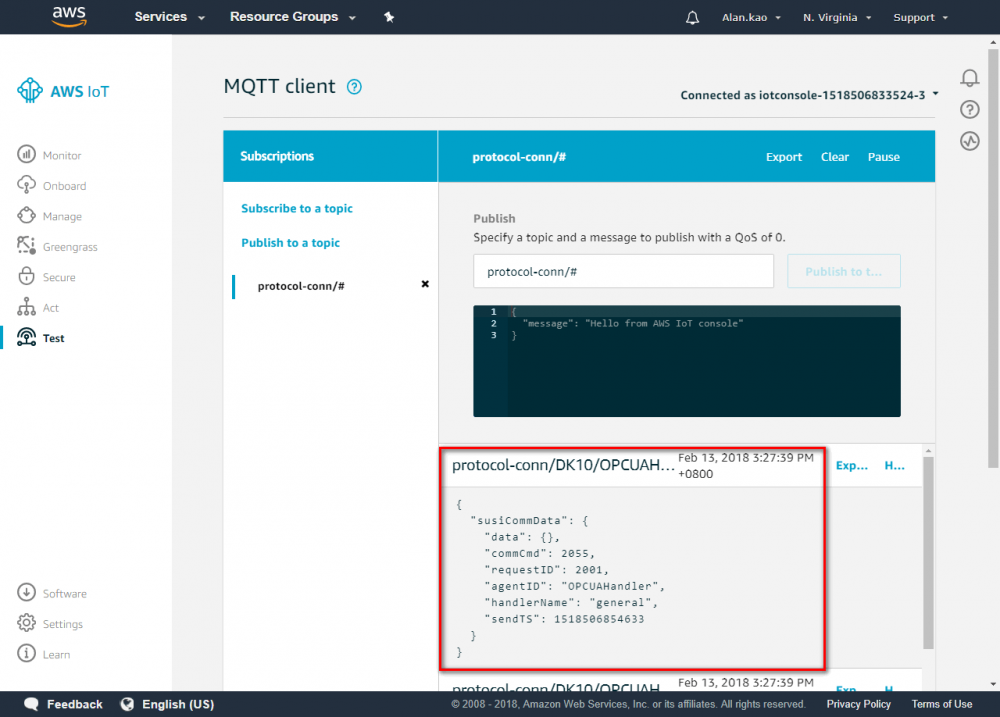
- Click NodeRED “Debug” tab, the sent messages will be displayed.
- Go back to AWS IoT menu
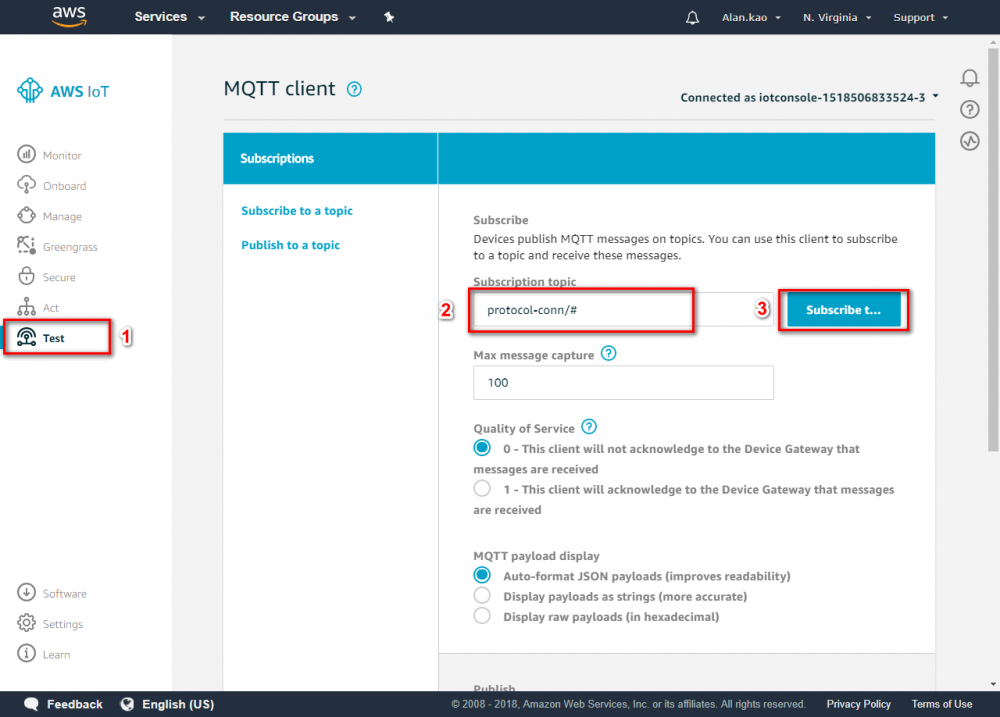
- click “Test” and enter Subscription topic click
- For more information, see https://docs.aws.amazon.com/iot/latest/developerguide/topics.html
- if your settings is correct, then you can see the message in this area.
Greengrass
Prerequisites
AWS Account
Linux Host
OS version : Ubuntu 16.04 x64
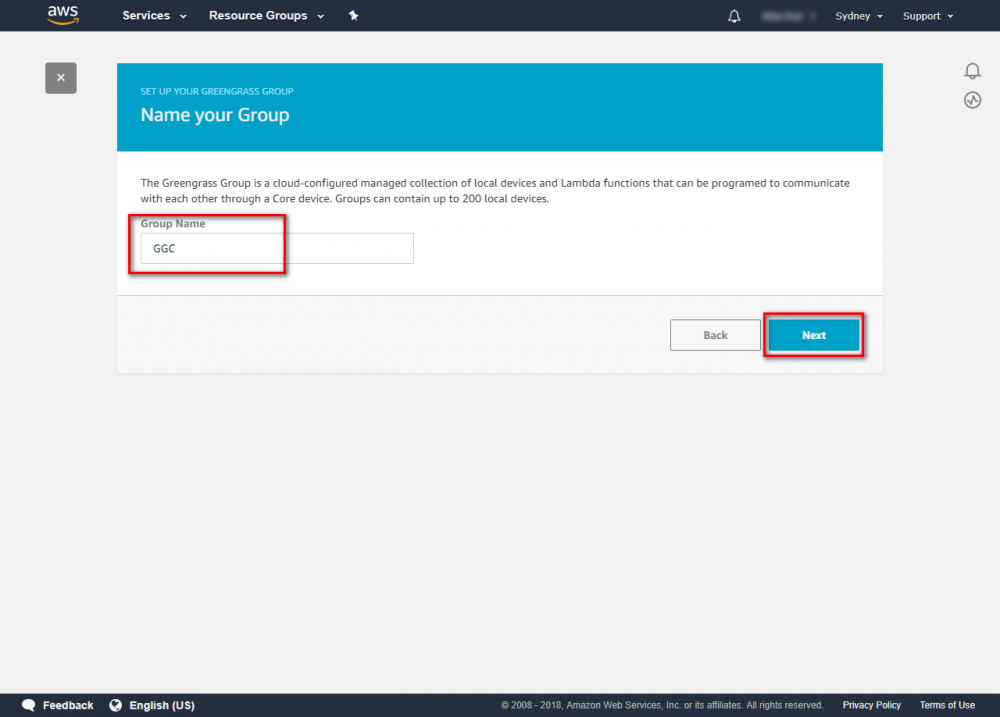
Create Greengrass Group
Using the AWS IoT console, create an AWS IoT thing, certificate, and policy for your AWS Greengrass core device:
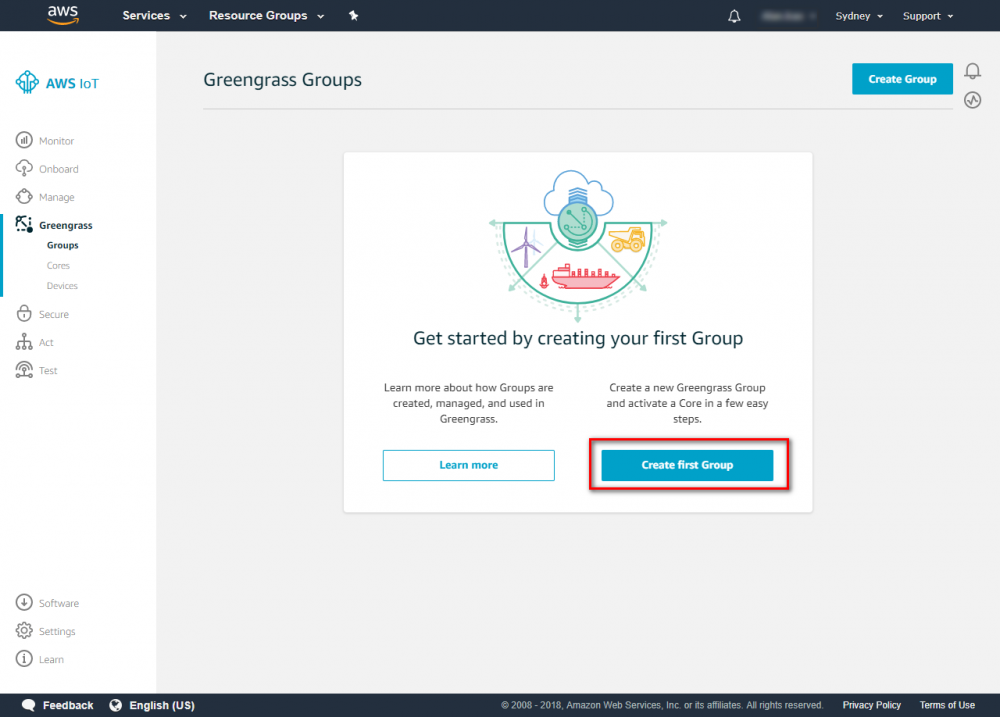
Step 1. Go to the AWS IoT console and click Greengrass.
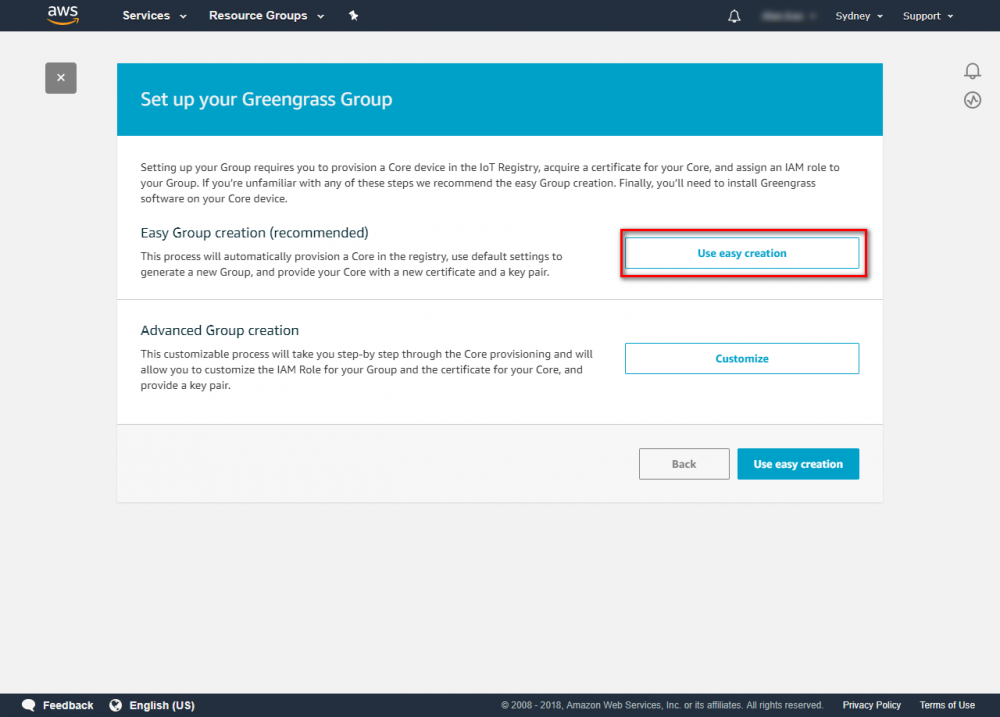
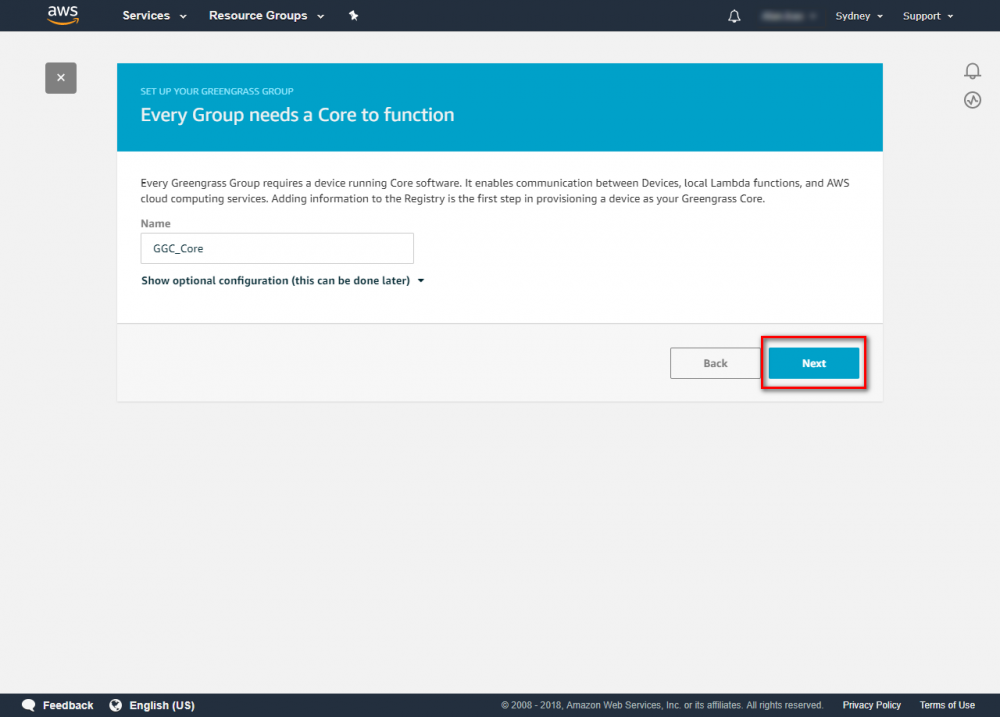
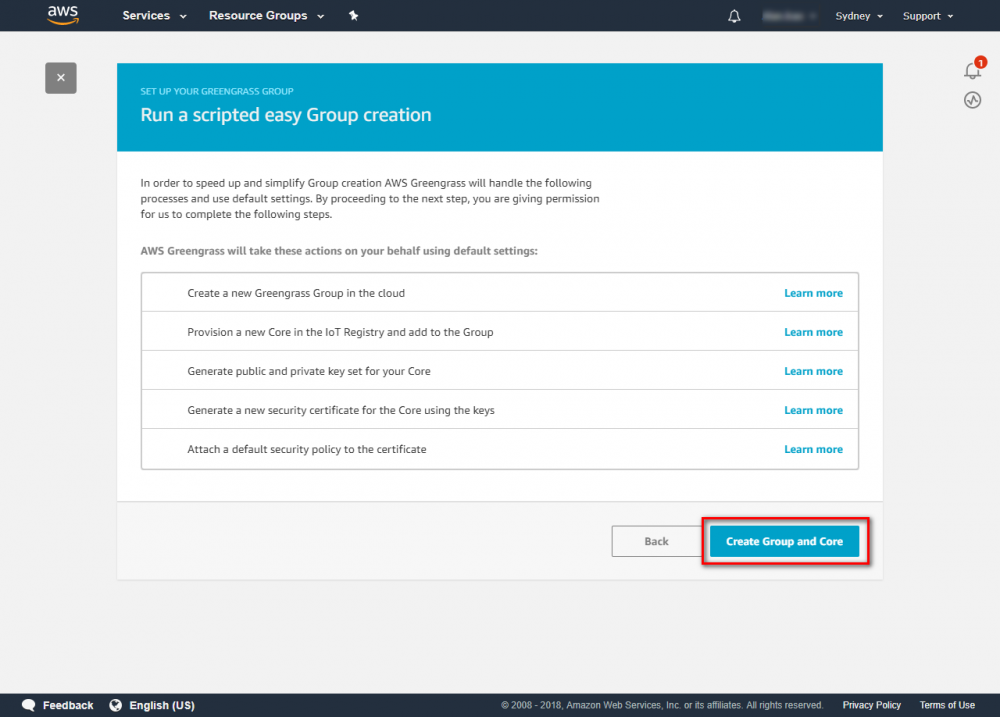
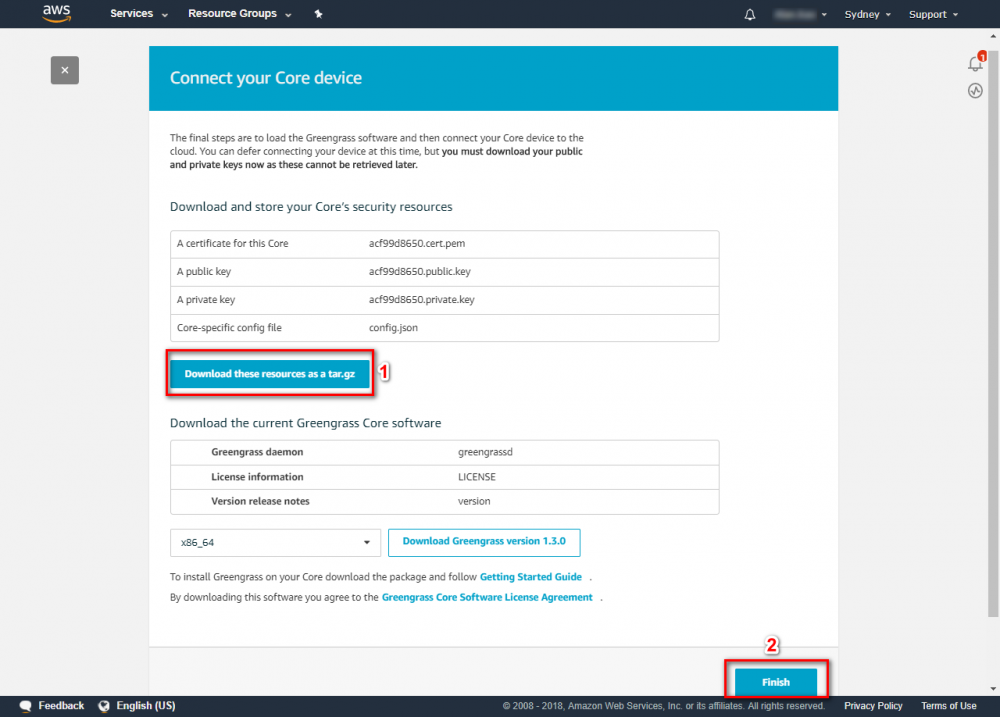
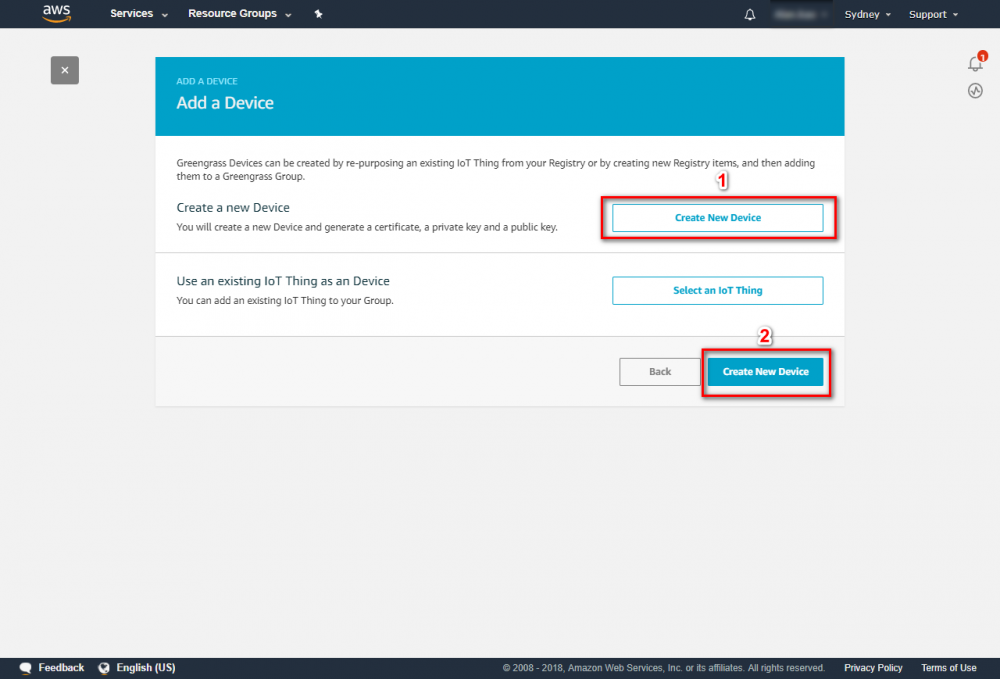
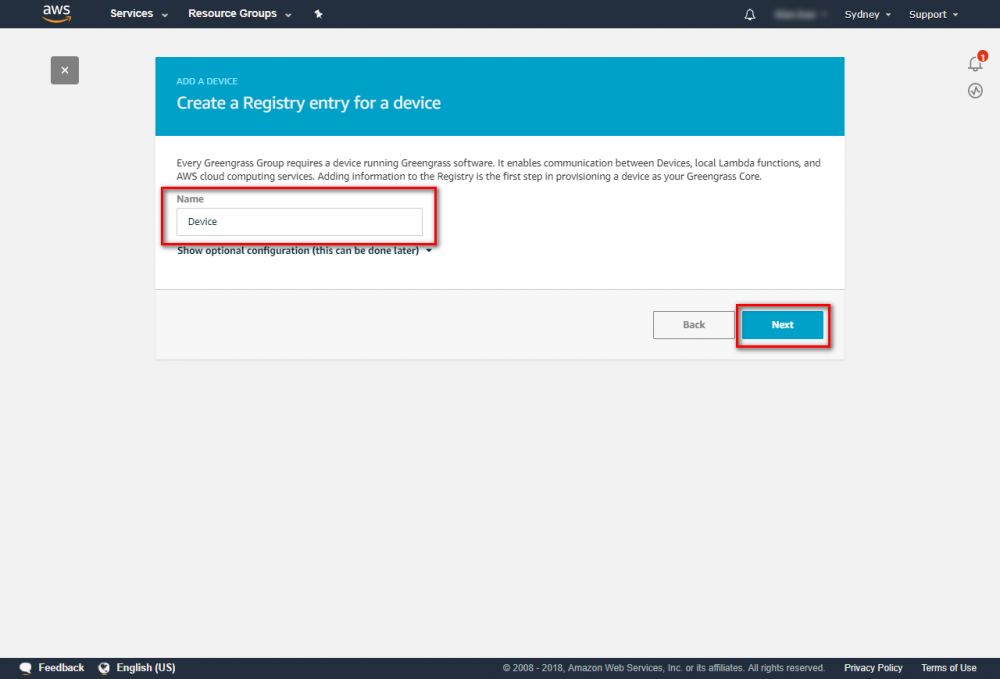
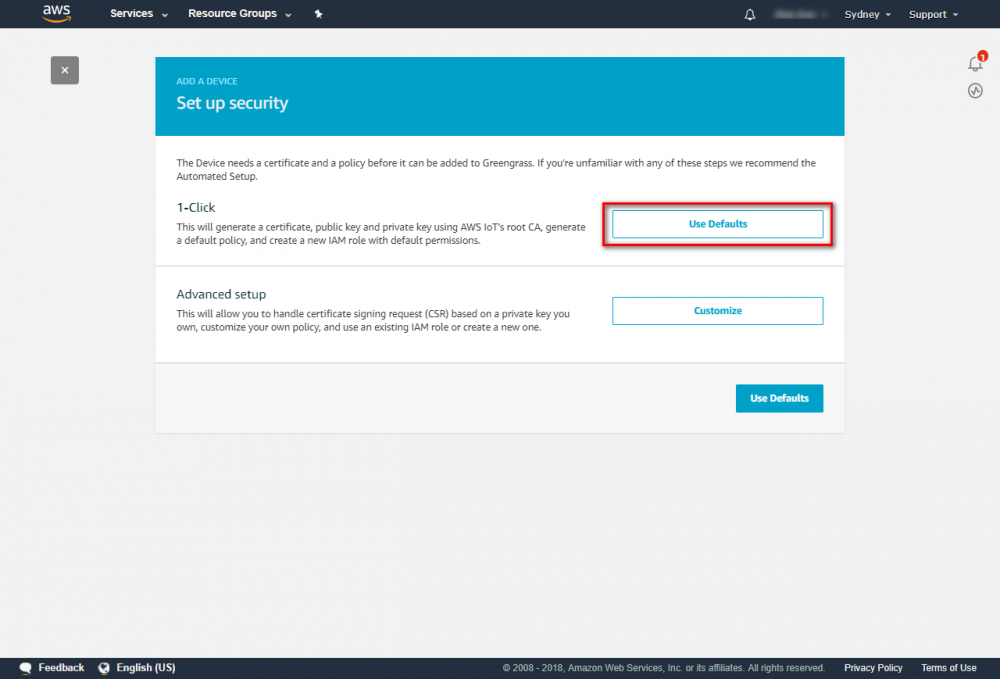
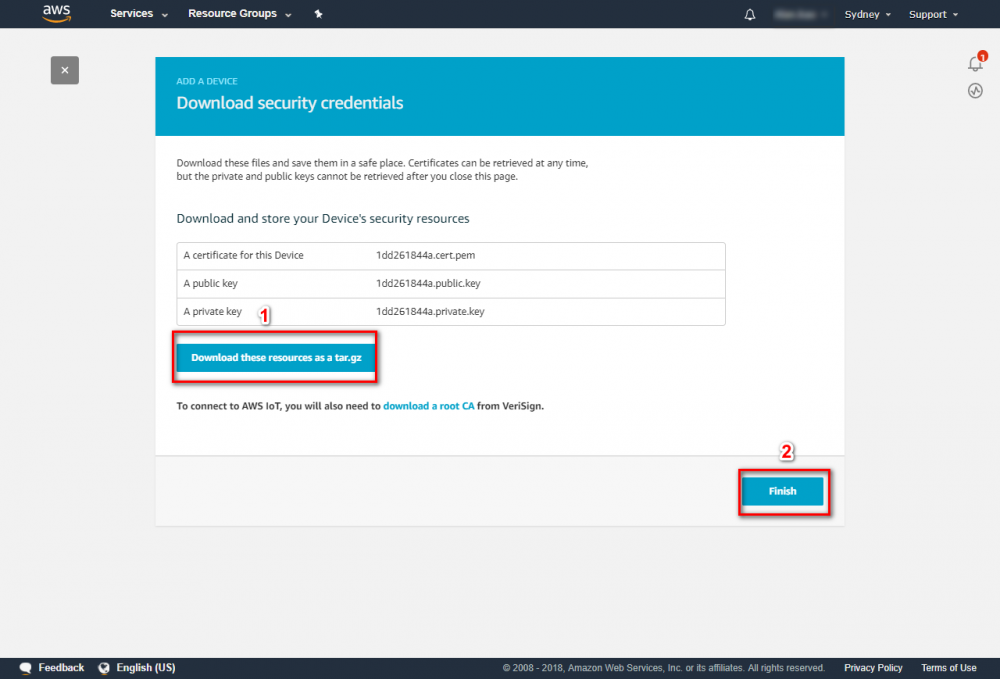
Step 2. Create an AWS Greengrass group and name it GGC Step 3. Create an AWS IoT for Greengrass core Step 3. Create an AWS IoT for Greengrass core Step 4. One-click to create Greengrass certificate and attach policy. Step 5. Download Certificate and Greengrass config.Setup Greengrass Group
To define your Greengrass group, follow these steps:
- Add devices to your group
- Add Lambda functions to your group
- Add subscriptions to your group
Add devices to your group
Step 1.Go to the AWS IoT console.
Step 2.In the navigation pane, select Greengrass and then Groups.
Step 3.Click on your group, GGC
Step 4.In the navigation pane, click Devices and then Add Device. Step 5. Enter AWS IoT Name Device and click Next Step 6. Using default setting to quick create access permissions and certificate. Step 7. Download certificate and finish this process
Add Lambda functions to your group
Step 1.Go to the AWS IoT console.
Step 2.In the navigation pane, select Greengrass and then Groups.
Step 3.Click on your group, GGC
Step 4.In the navigation pane, click Lambda and then Add Lambda.
Step 5.In the Lambda console, click Create function then the browser will go to the lambda page.Step 6.In the Name field, type the name of the Lambda function you are creating. In this case, lambda was named DK10_Lambda.
Step 7.In the Runtime drop down menu, select Python 2.7.
Step 8.In the Role drop down, select Choose an existing role. In the Existing role drop down, select any role. The role is not important because AWS Greengrass does not use it. If you do not have a role, choose Create a custom role and follow the steps.
Step 9.Click Create function.
Step 10.In the Function code section, select Upload a .ZIP file in the Code entry type drop down.
Step 11.Click Upload and select the corresponding zip file.
Step 12.Review the Lambda settings and click Save button at the top right.
Step 13.Publish a new version of the Lambda function from Actions > Publish new version.
Step 14.Click Publish in the Publish new version dialog. AWS Lambda creates a new version and assigns an increasing sequence number to it, 1 for the first version.
Step 15.Go back to Greengrass Lambda page
Step 16.Click Use existing Lambda.
Step 17.Select the DK10_Lambda you created.
Step 18.Click Next
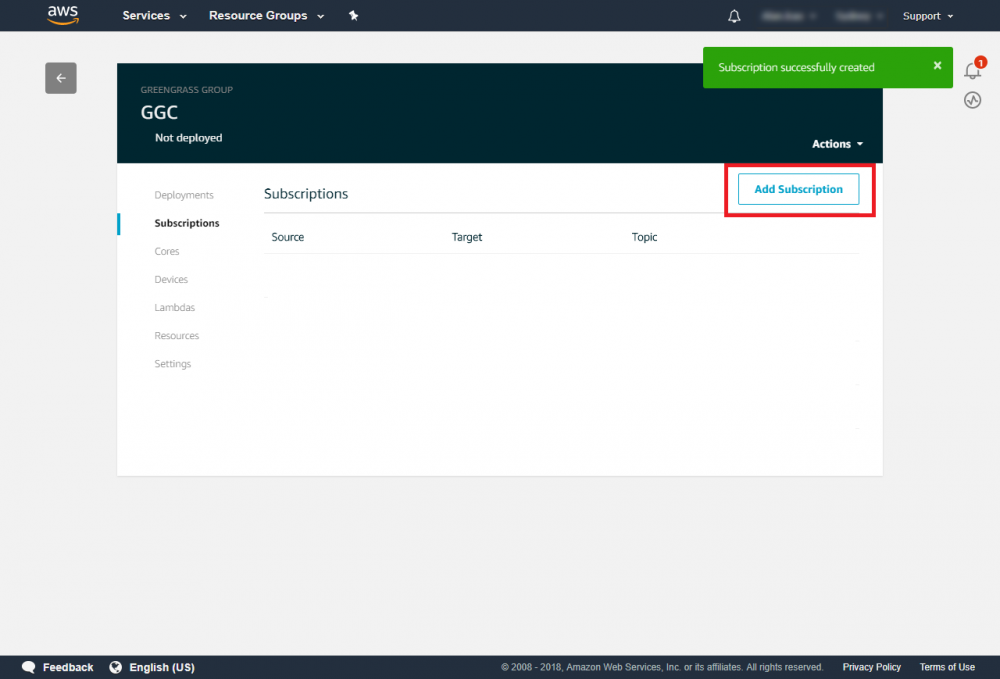
Step 19.Select Version 1 and click Finish .Add subscriptions to your group
Step 1.In the navigation pane, click Subscriptions and then Add Subscription.Step 2.Under Select a source, select the source of the subscription.
Step 3.Under Select a target, select the target of the subscription.
Step 4.Click Next.
Step 5.In the Optional topic filter, type the topic of the subscription.
Step 6.Click Next.
Step 7.Review the subscription information and click Finish to create it.
Run Greengrass core in your device
To configure your core to recognize the AWS IoT thing, update the /greengrass/config/config.json file. and /greengrass/certs.
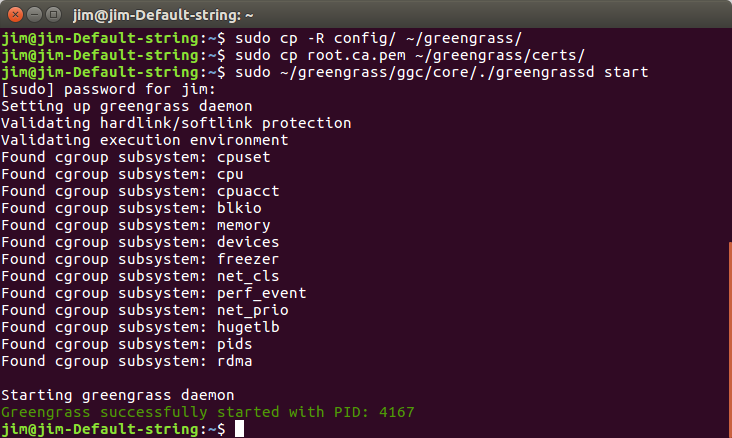
Copy certs and config with root permission
Step 1.sudo cp -R certs/ ~/<unzipped the path>/greengrass/
Step 2.sudo cp -R conf/ ~/<unzipped the path>/greengrass/
Step 3.sudo cp root.ca.pem ~/<unzipped the path>/greengrass/certs/
The Greengrass core software is installed inside the /greengrass directory of your device.
Step 1.Make sure your device is connected to the Internet.
Step 2.sudo ~/<your path>/greengrass/ggc/core/greengrassd start
Deploy your Greengrass group
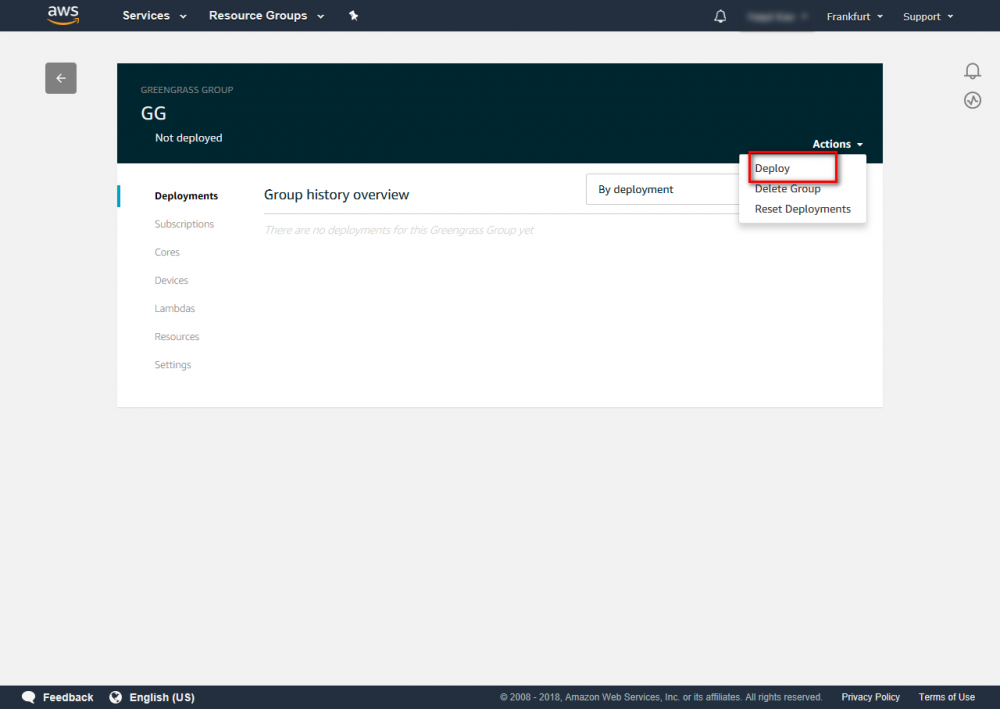
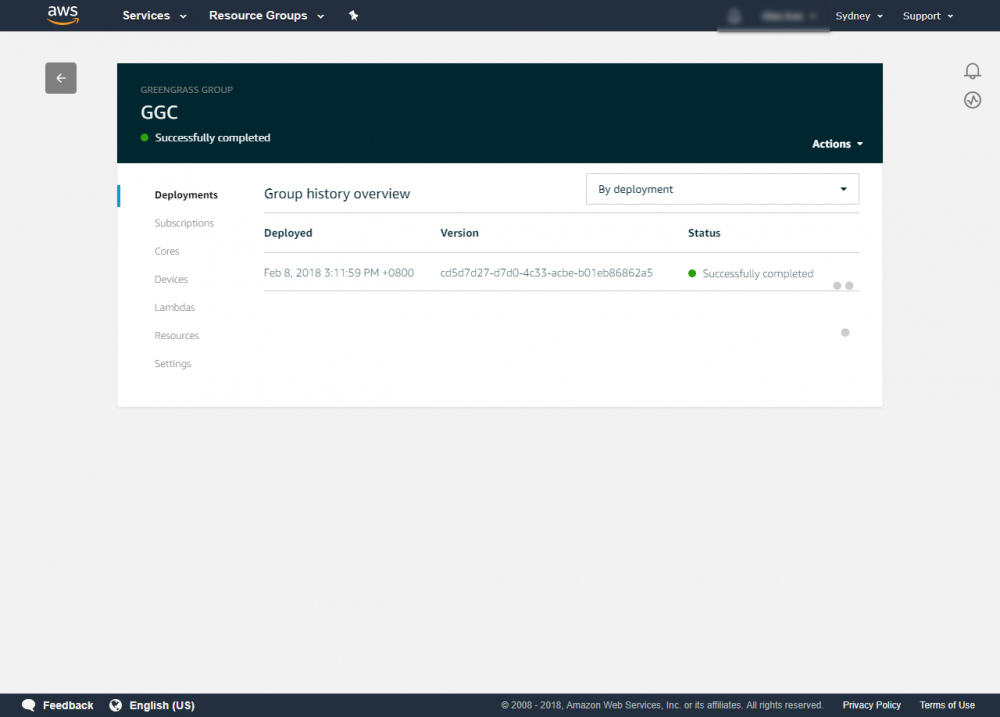
After running Greengrass core, you can deploy your Greengrass group to your device.
Step 1.Go to the AWS IoT console.
Step 2.In the navigation pane, select Greengrass and then Groups.
Step 3.Click on your group, GGC.
Step 4.In the navigation pane, click Deployments.
Step 5.Click Actions > Deploy.
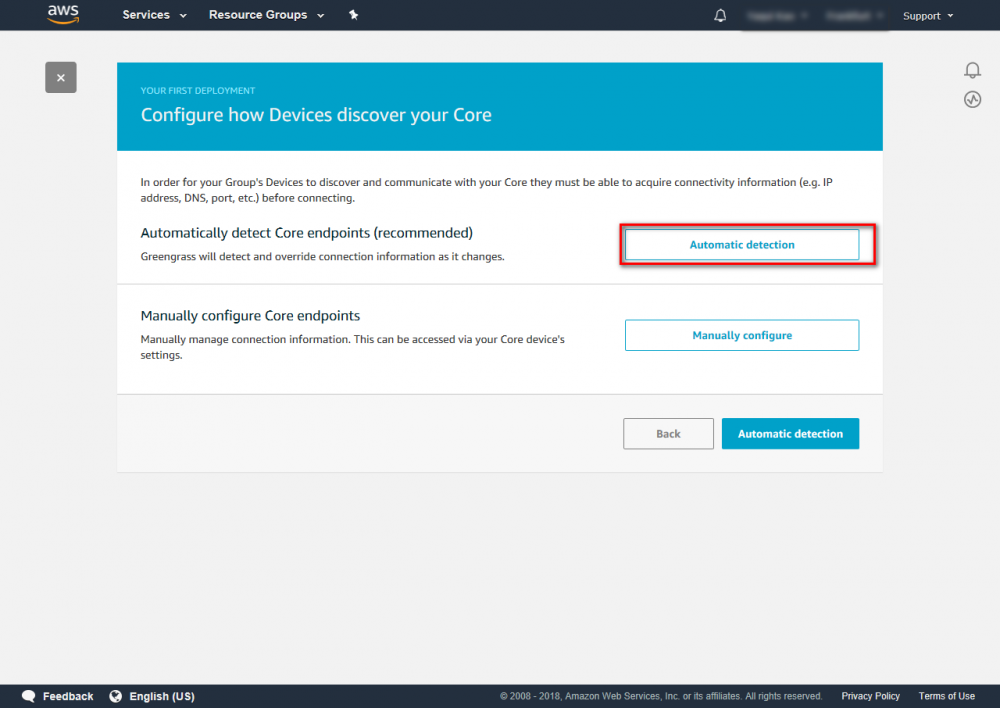
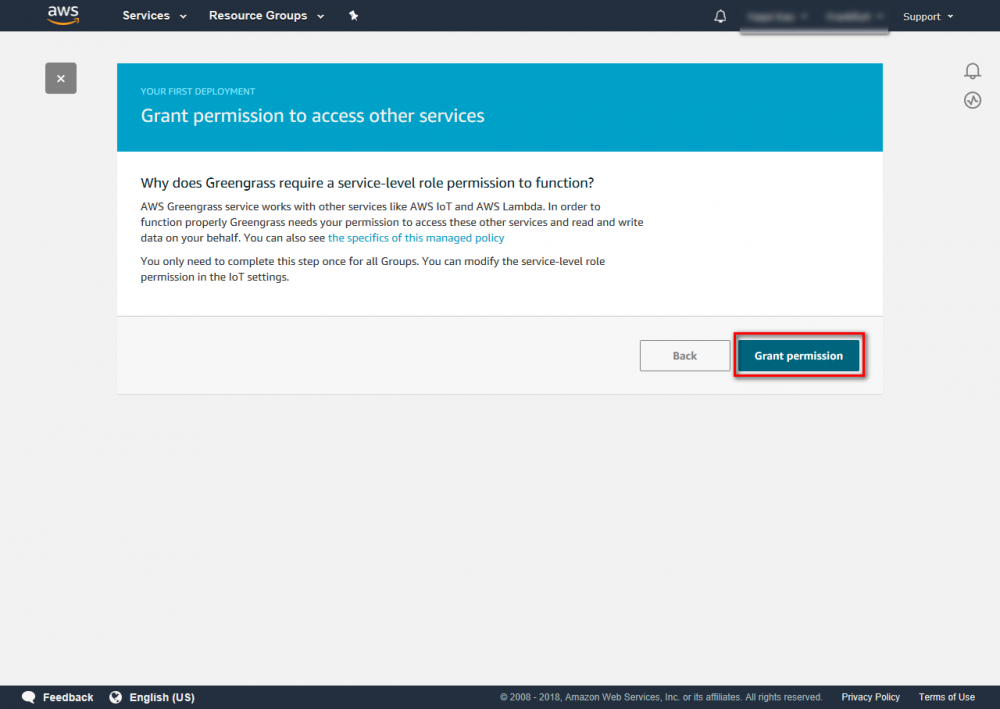
Step 6.In the Configure how Devices discover your Core select Automatic detection. Step 7.In the Grant permissions to access other services, click Grant permission. When the operation is complete, the Deployment successfully completed is displayed at the top of the page.
Set up your AWS IoT Things
When Greengrass group is deployed successful. You can setup AWS IoT Device which is defined in Greengrass group with Protocol Connector.
AWS IoT devices need certificates to authenticate with AWS IoT and retrieve the connectivity information of your Greengrass core. You downloaded these certificates in Add devices to your group Create device things.
Install your thing certificates
cp root-ca.pem <parent_absolute_path>/ProtocolConnectorSample/certs
cp <id>.pem.crt <parent_absolute_path>/ProtocolConnectorSample/certs
cp <id>-private.pem.key <parent_absolute_path>/ProtocolConnectorSample/certs
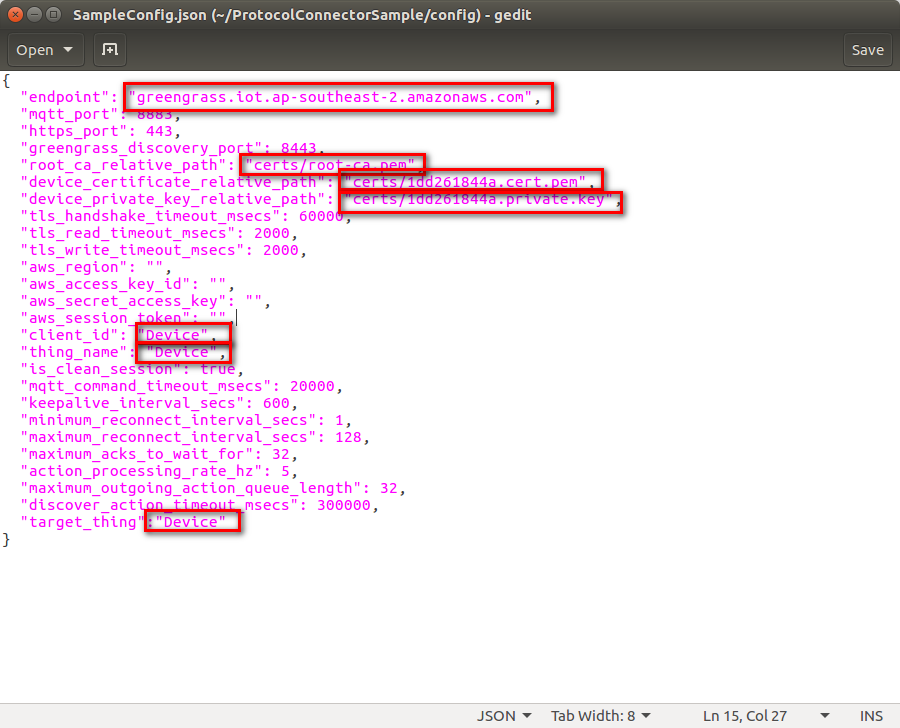
Configure the samples
Inside the ProtocolConnectorSample/config/ directory you can find the configuration files for your things:
Run the protocol connector sample
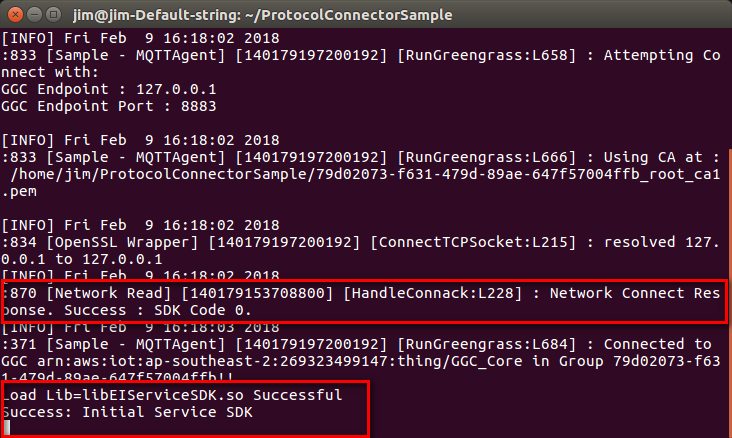
After setting AWS IoT you can execute protocol connector sample,
In the ProtocolConnectorSample folder
./MQTTAgent-sample
Edge Sense
Windows
Linux
Basic Requirment:
- Host OS must be Linux Distribution ( e.g. Ubuntu 14.04 / 16.04, ... )
- Docker Engine - Installation Guide ( Ubuntu, Debian, CentOS, Fedora, )
- Docker compose - Installation Guid
- Hardward: Advantech x86_64 Platforms ( e.g. ARK-2121L...)
How To Install and Run - Protocol Connector Docker Container Services
$git clone --branch installer-v1.0.1 https://github.com/ADVANTECH-Corp/docker-edgesense-image-x86.git . $cd docker // To deploy Services $./deploy // To install EI-Agent for EnSaaS $./deploy.sh connector EnSaaS
How to modify your server ID/Password and resart
# To modify your ConnAuth then save and exit # <ConnAuth>2b7555b4-4313-4320-8b3b-1140350ec279:928e36c5-b22a-4a03-8fcd-470eb61552c0;7tnorqqc20nf0dbldnamu3co4g</ConnAuth> $cd ../EdgeSense/AgentService/config/ $sudo vim agent_config.xml $docker restart ensaas-ei-agent
How to config Modbus Service and Restart Service
$cd ../EdgeSense/EService-Modbus/config $sudo vim Modbus_Handler.ini $docker stop service-modbus $docker start service-modbus
Release
Pages with broken file links