Difference between revisions of "IoTGateway/AWS/Greengrass"
Daniel.hung (talk | contribs) |
Daniel.hung (talk | contribs) |
||
| Line 130: | Line 130: | ||
2. Click Roles and "Create new role". | 2. Click Roles and "Create new role". | ||
| + | |||
| + | [[File:Aws-gg-8.png|400px|Aws-gg-8.png]] | ||
| + | |||
| + | 3. On “Select role type” page, find and choose “AWS Greengrass Role”. | ||
| + | |||
| + | [[File:Aws-gg-9.png|800px|Aws-gg-9.png]] | ||
| + | |||
| + | 4. On “Attach Policy” page, find and check "AWSGreengrassResourceAccessRolePolicy". | ||
| + | |||
| + | [[File:Aws-gg-10.png|800px|Aws-gg-10.png]] | ||
| + | |||
| + | 5. On the next page, fill in the Role name, e.g. ''GreengrassServiceRole''. Check that your policies are correct, and click "Create role" | ||
| + | |||
| + | [[File:Aws-gg-11.png|800px|Aws-gg-11.png]] | ||
| + | |||
| + | 6. Open your new role and take a note of the '''''Role ARN'''''as we need to use it in the next step. | ||
| + | |||
| + | [[File:Aws-gg-12.png|800px]] | ||
=== <font color="#0070c0">Get Connected to AWS</font> === | === <font color="#0070c0">Get Connected to AWS</font> === | ||
Revision as of 09:56, 6 September 2017
This article is written based on AWS (Amazon Web Services) Greengrass 1.0.0, and the target device is Advantech RSB-4760 (Qualcomm APQ8016 platform).
Set Up Environment
This section is referred to the AWS Greengrass document and AWS CLI document.
Debian 9 (Stretch)
1. Add ggc_user and ggc_group using the following commands:
sudo useradd ggc_user sudo groupadd ggc_group
2. Install missing dependencies using the following commands:
sudo apt-get update sudo apt-get install sqlite3
3. Set up cgroups
wget https://raw.githubusercontent.com/tianon/cgroupfs-mount/master/cgroupfs-mount chmod 777 cgroupfs-mount sudo bash ./cgroupfs-mount
4. Install Pip
curl -O https://bootstrap.pypa.io/get-pip.py python get-pip.py --user # Add an export command to your profile script, e.g. ~/.profile export PATH=~/.local/bin:$PATH # Load the profile into your current session source ~/.profile # Verify that pip is installed correctly pip --version
5. Installing the AWS CLI with Pip
pip install awscli --upgrade --user # Verify that the AWS CLI installed correctly aws --version
Set Up AWS Greengrass
This section is referred to this AWS Greengrass document.
Download the AWS Greengrass Core Software
Sign in to the AWS Management Console and navigate to the AWS IoT console. Then, download the AWS Greengrass Core Software from Software page.
Copy the tar file into target device, and use the following command to extract the tar file:
sudo tar -zxvf greengrass-platform-version.tar.gz -C /
- Where platform is either:
- linux-armv7l
- linux-x86-64
- linux-aarch64
PS: You are also able to download this AWS Greengrass core software in the next step.
Create an AWS Greengrass Group
Open the AWS IoT console and, in the navigation pane, choose Greengrass. On the Define a Greengrass group tile, choose Get Started.
On the Set up your Greengrass Group page, choose Use easy creation, and then follow the instructions. Finally, you can see the page as below.
Download the public/private key pairs & certificate, and keep them safe. When the download has completed choose Finish.
Install certificates on your Core device
1. Download the AWS IoT root CA certificate from Verisign.
2. Copy the Core's private key, certificate, and the AWS IoT root CA certificate into the /greengrass/configuration/certs directory of your device using the following names:
- cloud.pem.crt
- The Core certificate downloaded from the console,e.g. ce69fc71e9.cert.pem.
- cloud.pem.key
- The private key downloaded from the console, e.g. ce69fc71e9.private.key.
- root-ca.pem
- The AWS IoT root CA certificate from Symantec.
Create an IAM User and a Greengrass Service Role
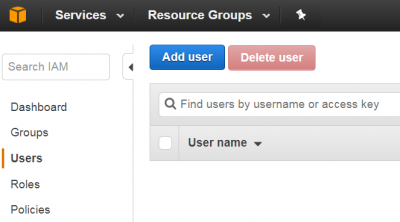
1. Go to IAM page from AWS Services.
2. Click Users and "Add user".
3. Input a user name you want, e.g. GreengrassUser. Select "Programmatic access”. Click “Next: Permissions”.
4. Select “Attach existing policies directly” and check “AdministratorAccess”. Click “Next: Review”.
5. Review your policy and click “Create user”.
6. Store your Access key ID and Secret access key in a safe place. You can also download a csv file which has the credentials.
Note: These credentials will be used later. If you leave this page, you will not be able to retrieve the secret access key.
Attach Greengrass Service Role
1. Go to IAM page from AWS Services.
2. Click Roles and "Create new role".
3. On “Select role type” page, find and choose “AWS Greengrass Role”.
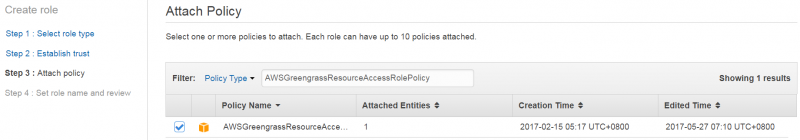
4. On “Attach Policy” page, find and check "AWSGreengrassResourceAccessRolePolicy".
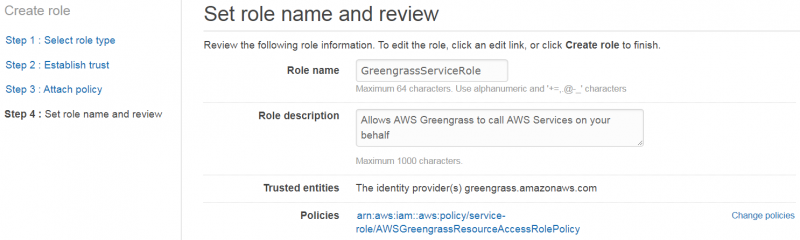
5. On the next page, fill in the Role name, e.g. GreengrassServiceRole. Check that your policies are correct, and click "Create role"
6. Open your new role and take a note of the Role ARNas we need to use it in the next step.