Difference between revisions of "IoTGateway/AWS/Greengrass"
Daniel.hung (talk | contribs) (Created page with "This article is written based on AWS (Amazon Web Services) Greengrass 1.0.0, and the target device is Advantech RSB-4760 (IoTGateway/BSP/Linux#APQ8016|Qualcomm APQ8016 platf...") |
Daniel.hung (talk | contribs) |
||
| (14 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
This article is written based on AWS (Amazon Web Services) Greengrass 1.0.0, and the target device is Advantech RSB-4760 ([[IoTGateway/BSP/Linux#APQ8016|Qualcomm APQ8016 platform]]). | This article is written based on AWS (Amazon Web Services) Greengrass 1.0.0, and the target device is Advantech RSB-4760 ([[IoTGateway/BSP/Linux#APQ8016|Qualcomm APQ8016 platform]]). | ||
| − | == Set | + | == <font color="#0070c0">Set up Environment</font> == |
| − | + | This section is referred to the [http://docs.aws.amazon.com/greengrass/latest/developerguide/prepare-annapurna.html AWS Greengrass document] and [http://docs.aws.amazon.com/cli/latest/userguide/awscli-install-linux.html AWS CLI document]. | |
| − | == | + | === <font color="#0070c0">Debian 9 (Stretch)</font> === |
| − | === | + | ==== <font color="#0070c0">To run the AWS Greengrass core software</font> ==== |
| − | + | 1. Add ggc_user and ggc_group using the following commands: | |
| − | + | sudo useradd ggc_user | |
| + | sudo groupadd ggc_group | ||
| − | + | 2. Install missing dependencies using the following commands: | |
| − | === Get Connected to AWS === | + | sudo apt-get update |
| + | sudo apt-get install sqlite3 | ||
| + | |||
| + | 3. Set up cgroups | ||
| + | |||
| + | wget [https://raw.githubusercontent.com/tianon/cgroupfs-mount/master/cgroupfs-mount https://raw.githubusercontent.com/tianon/cgroupfs-mount/master/cgroupfs-mount] | ||
| + | chmod 777 cgroupfs-mount | ||
| + | sudo bash ./cgroupfs-mount | ||
| + | |||
| + | 4. Install Pip | ||
| + | |||
| + | curl -O [https://bootstrap.pypa.io/get-pip.py https://bootstrap.pypa.io/get-pip.py] | ||
| + | python get-pip.py --user | ||
| + | |||
| + | # Add an export command to your profile script, e.g. ~/.profile | ||
| + | export PATH=~/.local/bin:$PATH | ||
| + | |||
| + | # Load the profile into your current session | ||
| + | source ~/.profile | ||
| + | |||
| + | # Verify that pip is installed correctly | ||
| + | pip --version | ||
| + | |||
| + | The Pip version should be like this. | ||
| + | |||
| + | pip 9.0.1 from /root/.local/lib/python2.7/site-packages (python 2.7) | ||
| + | |||
| + | 5. Installing the AWS CLI with Pip | ||
| + | |||
| + | pip install awscli --upgrade --user | ||
| + | |||
| + | # Verify that the AWS CLI installed correctly | ||
| + | aws --version | ||
| + | |||
| + | The AWS CLI version should be like this. | ||
| + | |||
| + | aws-cli/1.11.146 Python/2.7.13 Linux/4.4.38-4760LIV1090 botocore/1.7.4 | ||
| + | |||
| + | ==== <font color="#0070c0">To use the AWS IoT Device SDK for C++</font> ==== | ||
| + | |||
| + | You have to install the following additional packages. | ||
| + | |||
| + | *cmake | ||
| + | *git | ||
| + | *openssl-1.0.2g | ||
| + | *libssl-dev | ||
| + | |||
| + | Please check the [http://docs.aws.amazon.com/greengrass/latest/developerguide/prepare-annapurna.html AWS Greengrass document] for details. | ||
| + | |||
| + | '''Note:''' It seems OK to install the ''openssl ''& ''libssl-dev ''via <code>apt-get install</code> directly. | ||
| + | |||
| + | == <font color="#0070c0">Set up AWS Greengrass</font> == | ||
| + | |||
| + | This section is referred to this [http://docs.aws.amazon.com/greengrass/latest/developerguide/gg-setup.html AWS Greengrass document]. | ||
| + | |||
| + | === <font color="#0070c0">Download the AWS Greengrass Core Software</font> === | ||
| + | |||
| + | Sign in to the [https://console.aws.amazon.com AWS Management Console] and navigate to the '''AWS IoT''' console. Then, download the [https://us-west-2.console.aws.amazon.com/iotv2/home?region=us-west-2#/software AWS Greengrass Core Software] from '''Software''' page. | ||
| + | |||
| + | Copy the tar file into target device, and use the following command to extract the tar file: | ||
| + | |||
| + | sudo tar -zxvf greengrass-<span style="color:purple">platform</span>-<span style="color:purple">version</span>.tar.gz -C / | ||
| + | |||
| + | :Where <span style="color:purple">platform</span> is either: | ||
| + | :*''linux-armv7l'' | ||
| + | :*''linux-x86-64'' | ||
| + | :*''linux-aarch64'' | ||
| + | |||
| + | '''PS:''' You are also able to download this AWS Greengrass core software in the next step. | ||
| + | |||
| + | === <font color="#0070c0">Set up AWS Greengrass Group</font> === | ||
| + | |||
| + | ==== <font color="#0070c0">Create Greengrass Group & Certificates</font> ==== | ||
| + | |||
| + | 1. Open the AWS IoT console and, in the navigation pane, choose '''Greengrass'''. On the '''Define a Greengrass group''' tile, choose '''Get Started'''. | ||
| + | |||
| + | [[File:Aws-gg-1.png|800px|Aws-gg-1.png]] | ||
| + | |||
| + | 2. On the '''Set up your Greengrass Group''' page, choose '''Use easy creation''', and then follow the instructions. Finally, you can see the page as below. | ||
| + | |||
| + | Download the public/private key pairs & certificate, and keep them safe. When the download has completed choose '''Finish'''. | ||
| + | |||
| + | ''' Note: <font color="red">[Important!]</font> '''These credentials will be used later. If you leave this page, you will '''not '''be able to retrieve the key pairs & certificate. | ||
| + | |||
| + | [[File:Aws-gg-2.png|600px|Aws-gg-2.png]] | ||
| + | |||
| + | ==== <font color="#0070c0">Install Certificates on Your Core Device</font> ==== | ||
| + | |||
| + | 1. Download the [http://www.symantec.com/content/en/us/enterprise/verisign/roots/VeriSign-Class%203-Public-Primary-Certification-Authority-G5.pem AWS IoT root CA certificate] from Verisign. | ||
| + | |||
| + | 2. Copy the Core's private key, certificate, and the AWS IoT root CA certificate into the <code>/greengrass/configuration/certs</code> directory of your device using the following names: | ||
| + | |||
| + | : | ||
| + | |||
| + | *'''''cloud.pem.crt''''' | ||
| + | |||
| + | ::The Core certificate downloaded from the console,e.g. ce69fc71e9.cert.pem. | ||
| + | |||
| + | : | ||
| + | |||
| + | *'''''cloud.pem.key''''' | ||
| + | |||
| + | ::The private key downloaded from the console, e.g. ce69fc71e9.private.key. | ||
| + | |||
| + | : | ||
| + | |||
| + | *'''''root-ca.pem''''' | ||
| + | |||
| + | ::The AWS IoT root CA certificate from Symantec. | ||
| + | |||
| + | === <font color="#0070c0">Create an IAM User</font> === | ||
| + | |||
| + | 1. Go to '''IAM''' page from AWS Services. | ||
| + | |||
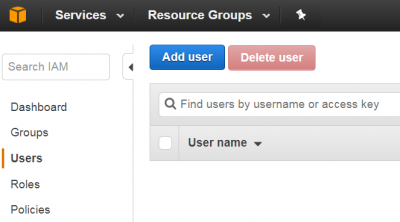
| + | 2. Click Users and "Add user". | ||
| + | |||
| + | [[File:Aws-gg-3.png|400px|Aws-gg-3.png]] | ||
| + | |||
| + | 3. Input a user name you want, e.g. ''GreengrassUser''. Select "Programmatic access”. Click “Next: Permissions”. | ||
| + | |||
| + | [[File:Aws-gg-4.png|800px|Aws-gg-4.png]] | ||
| + | |||
| + | 4. Select “Attach existing policies directly” and check “AdministratorAccess”. Click “Next: Review”. | ||
| + | |||
| + | [[File:Aws-gg-5.png|800px|Aws-gg-5.png]] | ||
| + | |||
| + | 5. Review and click “Create user”. | ||
| + | |||
| + | [[File:Aws-gg-6.png|800px|Aws-gg-6.png]] | ||
| + | |||
| + | 6. Store your '''''Access key ID'''''and '''''Secret access key''''' in a safe place. You can also download a csv file which has the credentials. | ||
| + | |||
| + | '''Note: <font color="red">[Important!]</font> '''These credentials will be used later. If you leave this page, you will '''not '''be able to retrieve the secret access key. | ||
| + | |||
| + | [[File:Aws-gg-7.png|800px|Aws-gg-7.png]] | ||
| + | |||
| + | === <font color="#0070c0">Set up Greengrass Service Role</font> === | ||
| + | |||
| + | ==== <font color="#0070c0">Create a Greengrass Service Role</font> ==== | ||
| + | |||
| + | 1. Go to '''IAM '''page from AWS Services. | ||
| + | |||
| + | 2. Click Roles and "Create new role". | ||
| + | |||
| + | [[File:Aws-gg-8.png|400px|Aws-gg-8.png]] | ||
| + | |||
| + | 3. On “Select role type” page, find and choose “AWS Greengrass Role”. | ||
| + | |||
| + | [[File:Aws-gg-9.png|800px|Aws-gg-9.png]] | ||
| + | |||
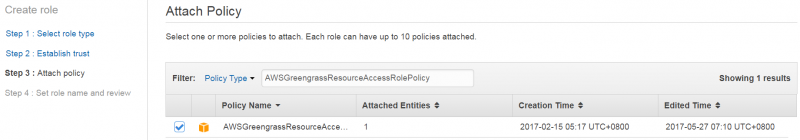
| + | 4. On “Attach Policy” page, find and check "AWSGreengrassResourceAccessRolePolicy". | ||
| + | |||
| + | [[File:Aws-gg-10.png|800px|Aws-gg-10.png]] | ||
| + | |||
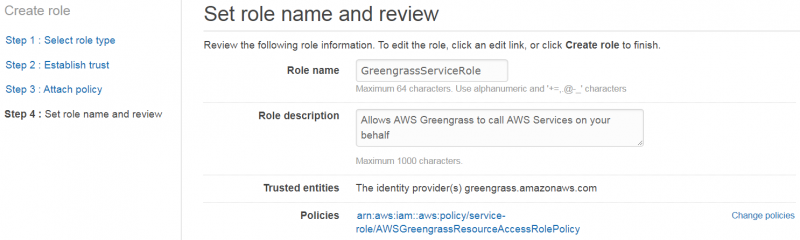
| + | 5. On the next page, fill in the Role name, e.g. ''GreengrassServiceRole''. Check that your policies are correct, and click "Create role" | ||
| + | |||
| + | [[File:Aws-gg-11.png|800px|Aws-gg-11.png]] | ||
| + | |||
| + | 6. Open your new role and take a note of the '''''Role ARN '''''as we need to use it in the next step. | ||
| + | |||
| + | [[File:Aws-gg-12.png|800px|Aws-gg-12.png]] | ||
| + | |||
| + | ==== <font color="#0070c0">Attach Greengrass Service Role</font> ==== | ||
| + | |||
| + | 1. Configure your AWS CLI first, if need. | ||
| + | |||
| + | aws configure | ||
| + | |||
| + | Then, input the information we collect in previous steps. | ||
| + | |||
| + | AWS Access Key ID [None]: <your Access key ID> | ||
| + | AWS Secret Access Key [None]: <your Secret access key> | ||
| + | Default region name [None]: us-west-2 | ||
| + | Default output format [None]: <press enter> | ||
| + | |||
| + | 2. Associate service role to your account. | ||
| + | |||
| + | aws greengrass associate-service-role-to-account --role-arn <your Role ARN> | ||
| + | |||
| + | For example, you may do the commands like this. | ||
| + | |||
| + | aws greengrass associate-service-role-to-account --role-arn arn:aws:iam::395741104517:role/GreengrassServiceRole | ||
| + | |||
| + | '''Note:''' If you do not have <code>aws greengrass</code> command, please upgrade AWS CLI to '''''1.11.100'''''or later. | ||
| + | |||
| + | === <font color="#0070c0">Get Connected to AWS</font> === | ||
| + | |||
| + | ==== <font color="#0070c0">Configure AWS Greengrass Core</font> ==== | ||
| + | |||
| + | 1. Go to '''Greengrass Groups''' page from AWS IoT console. | ||
| + | |||
| + | 2. Choose your Greengrass group, and select '''Core '''page. | ||
| + | |||
| + | [[File:Aws-gg-13.png|600px|Aws-gg-13.png]] | ||
| + | |||
| + | 3. Copy the Thing ARN of your Core. | ||
| + | |||
| + | [[File:Aws-gg-14.png|600px|Aws-gg-14.png]] | ||
| + | |||
| + | 4. On your target device, open the file <code>/greengrass/configuration/config.json</code>. It will initially look like this: | ||
| + | |||
| + | { | ||
| + | "CoreThing": { | ||
| + | "caPath": "<ROOT_CA_PEM_HERE>", | ||
| + | "certPath": "<CLOUD_PEM_CRT_HERE>", | ||
| + | "keyPath": "<CLOUD_PEM_KEY_HERE>", | ||
| + | "thingArn": "<THING_ARN_HERE>", | ||
| + | "iotHost": "<HOST_PREFIX_HERE>.iot.<AWS_REGION_HERE>.amazonaws.com", | ||
| + | "ggHost": "greengrass.iot.<AWS_REGION_HERE>.amazonaws.com" | ||
| + | }, | ||
| + | "runtime": { | ||
| + | "cGroup": { | ||
| + | "useSystemd": "[yes|no]" | ||
| + | } | ||
| + | } | ||
| + | } | ||
| + | |||
| + | Update the file with the following content: | ||
| + | |||
| + | { | ||
| + | "CoreThing": { | ||
| + | "caPath": "<font color="red">root-ca.pem</font>", | ||
| + | "certPath": "<font color="red">cloud.pem.crt</font>", | ||
| + | "keyPath": "<font color="red">cloud.pem.key</font>", | ||
| + | "thingArn": <font color="red"><your Thing ARN></font>, | ||
| + | "iotHost": "<font color="red"><HOST_PREFIX_HERE></font>.iot.<font color="red">us-west-2</font>.amazonaws.com", | ||
| + | "ggHost": "greengrass.iot.<font color="red">us-west-2</font>.amazonaws.com", | ||
| + | "keepAlive": 600 | ||
| + | }, | ||
| + | "runtime": { | ||
| + | "cGroup": { | ||
| + | "useSystemd": "<font color="red">yes</font>" | ||
| + | } | ||
| + | } | ||
| + | } | ||
| + | |||
| + | ==== <font color="#0070c0">Enable Hardlink/Softlink Protection</font> ==== | ||
| + | |||
| + | 1. If you encounter an error like <code>Insecure configuration detected: No hardlink/softlink protection</code>, you have to do command below, before starting Greengrass core software. | ||
| + | |||
| + | vi /etc/sysctl.conf | ||
| + | |||
| + | Modify the following items. | ||
| + | |||
| + | kernel.printk = 7 7 1 7 | ||
| + | fs.protected_hardlinks = 1 | ||
| + | fs.protected_symlinks = 1 | ||
| + | |||
| + | 2. Reload the new configuration. | ||
| + | |||
| + | sysctl -p | ||
| + | |||
| + | ==== <font color="#0070c0">Run the AWS Greengrass Core Software</font> ==== | ||
| + | |||
| + | 1. Make sure your AWS Greengrass core device is connected to the internet. | ||
| + | |||
| + | Then, start your Greengrass Core to connect it to the cloud by running: | ||
| + | |||
| + | sudo /greengrass/greengrassd start | ||
| + | |||
| + | If the Greengass daemon starts successfully you should see the following output: | ||
| + | |||
| + | Setting up greengrass daemon | ||
| + | Validating execution environment | ||
| + | Found cgroup subsystem: cpuset | ||
| + | Found cgroup subsystem: cpu | ||
| + | Found cgroup subsystem: cpuacct | ||
| + | Found cgroup subsystem: blkio | ||
| + | Found cgroup subsystem: memory | ||
| + | Found cgroup subsystem: devices | ||
| + | Found cgroup subsystem: freezer | ||
| + | Found cgroup subsystem: net_cls | ||
| + | Found cgroup subsystem: perf_event | ||
| + | Found cgroup subsystem: net_prio | ||
| + | Found cgroup subsystem: hugetlb | ||
| + | Found cgroup subsystem: pids | ||
| + | |||
| + | Starting greengrass daemon..... | ||
| + | <font color="green">Greengrass daemon started with PID: 2697</font> | ||
| + | |||
| + | 2. To see if your AWS Greengrass core device is running, check that <code>/greengrass/crash.log</code> is empty and <code>/greengrass/var/log/system/runtime.log</code> has text like the following: | ||
| + | |||
| + | [INFO]-Deployment agent connected to cloud | ||
| + | [INFO]-Subscribed to topic $aws/things/GGC_Thing-gda/shadow/update/delta | ||
| + | [INFO]-Subscribed to topic $aws/things/GGC_Thing-gda/shadow/get/accepted | ||
| + | |||
| + | This text means that your AWS Greengrass core device is connected to AWS IoT and waiting for a deployment to take place. | ||
| + | |||
| + | 3. Open the AWS IoT console and check the '''Dashboard '''page. You should see the connections status. | ||
| + | |||
| + | [[File:Aws-gg-15.png|800px]] | ||
| + | |||
| + | PS. The date & time are not matched in '''Week '''mode. You can switch to '''Day''' or '''Hour '''for correct records. | ||
Latest revision as of 02:28, 7 September 2017
This article is written based on AWS (Amazon Web Services) Greengrass 1.0.0, and the target device is Advantech RSB-4760 (Qualcomm APQ8016 platform).
Contents
Set up Environment
This section is referred to the AWS Greengrass document and AWS CLI document.
Debian 9 (Stretch)
To run the AWS Greengrass core software
1. Add ggc_user and ggc_group using the following commands:
sudo useradd ggc_user sudo groupadd ggc_group
2. Install missing dependencies using the following commands:
sudo apt-get update sudo apt-get install sqlite3
3. Set up cgroups
wget https://raw.githubusercontent.com/tianon/cgroupfs-mount/master/cgroupfs-mount chmod 777 cgroupfs-mount sudo bash ./cgroupfs-mount
4. Install Pip
curl -O https://bootstrap.pypa.io/get-pip.py python get-pip.py --user # Add an export command to your profile script, e.g. ~/.profile export PATH=~/.local/bin:$PATH # Load the profile into your current session source ~/.profile # Verify that pip is installed correctly pip --version
The Pip version should be like this.
pip 9.0.1 from /root/.local/lib/python2.7/site-packages (python 2.7)
5. Installing the AWS CLI with Pip
pip install awscli --upgrade --user # Verify that the AWS CLI installed correctly aws --version
The AWS CLI version should be like this.
aws-cli/1.11.146 Python/2.7.13 Linux/4.4.38-4760LIV1090 botocore/1.7.4
To use the AWS IoT Device SDK for C++
You have to install the following additional packages.
- cmake
- git
- openssl-1.0.2g
- libssl-dev
Please check the AWS Greengrass document for details.
Note: It seems OK to install the openssl & libssl-dev via apt-get install directly.
Set up AWS Greengrass
This section is referred to this AWS Greengrass document.
Download the AWS Greengrass Core Software
Sign in to the AWS Management Console and navigate to the AWS IoT console. Then, download the AWS Greengrass Core Software from Software page.
Copy the tar file into target device, and use the following command to extract the tar file:
sudo tar -zxvf greengrass-platform-version.tar.gz -C /
- Where platform is either:
- linux-armv7l
- linux-x86-64
- linux-aarch64
PS: You are also able to download this AWS Greengrass core software in the next step.
Set up AWS Greengrass Group
Create Greengrass Group & Certificates
1. Open the AWS IoT console and, in the navigation pane, choose Greengrass. On the Define a Greengrass group tile, choose Get Started.
2. On the Set up your Greengrass Group page, choose Use easy creation, and then follow the instructions. Finally, you can see the page as below.
Download the public/private key pairs & certificate, and keep them safe. When the download has completed choose Finish.
Note: [Important!] These credentials will be used later. If you leave this page, you will not be able to retrieve the key pairs & certificate.
Install Certificates on Your Core Device
1. Download the AWS IoT root CA certificate from Verisign.
2. Copy the Core's private key, certificate, and the AWS IoT root CA certificate into the /greengrass/configuration/certs directory of your device using the following names:
- cloud.pem.crt
- The Core certificate downloaded from the console,e.g. ce69fc71e9.cert.pem.
- cloud.pem.key
- The private key downloaded from the console, e.g. ce69fc71e9.private.key.
- root-ca.pem
- The AWS IoT root CA certificate from Symantec.
Create an IAM User
1. Go to IAM page from AWS Services.
2. Click Users and "Add user".
3. Input a user name you want, e.g. GreengrassUser. Select "Programmatic access”. Click “Next: Permissions”.
4. Select “Attach existing policies directly” and check “AdministratorAccess”. Click “Next: Review”.
5. Review and click “Create user”.
6. Store your Access key IDand Secret access key in a safe place. You can also download a csv file which has the credentials.
Note: [Important!] These credentials will be used later. If you leave this page, you will not be able to retrieve the secret access key.
Set up Greengrass Service Role
Create a Greengrass Service Role
1. Go to IAM page from AWS Services.
2. Click Roles and "Create new role".
3. On “Select role type” page, find and choose “AWS Greengrass Role”.
4. On “Attach Policy” page, find and check "AWSGreengrassResourceAccessRolePolicy".
5. On the next page, fill in the Role name, e.g. GreengrassServiceRole. Check that your policies are correct, and click "Create role"
6. Open your new role and take a note of the Role ARN as we need to use it in the next step.
Attach Greengrass Service Role
1. Configure your AWS CLI first, if need.
aws configure
Then, input the information we collect in previous steps.
AWS Access Key ID [None]: <your Access key ID> AWS Secret Access Key [None]: <your Secret access key> Default region name [None]: us-west-2 Default output format [None]: <press enter>
2. Associate service role to your account.
aws greengrass associate-service-role-to-account --role-arn <your Role ARN>
For example, you may do the commands like this.
aws greengrass associate-service-role-to-account --role-arn arn:aws:iam::395741104517:role/GreengrassServiceRole
Note: If you do not have aws greengrass command, please upgrade AWS CLI to 1.11.100or later.
Get Connected to AWS
Configure AWS Greengrass Core
1. Go to Greengrass Groups page from AWS IoT console.
2. Choose your Greengrass group, and select Core page.
3. Copy the Thing ARN of your Core.
4. On your target device, open the file /greengrass/configuration/config.json. It will initially look like this:
{
"CoreThing": {
"caPath": "<ROOT_CA_PEM_HERE>",
"certPath": "<CLOUD_PEM_CRT_HERE>",
"keyPath": "<CLOUD_PEM_KEY_HERE>",
"thingArn": "<THING_ARN_HERE>",
"iotHost": "<HOST_PREFIX_HERE>.iot.<AWS_REGION_HERE>.amazonaws.com",
"ggHost": "greengrass.iot.<AWS_REGION_HERE>.amazonaws.com"
},
"runtime": {
"cGroup": {
"useSystemd": "[yes|no]"
}
}
}
Update the file with the following content:
{
"CoreThing": {
"caPath": "root-ca.pem",
"certPath": "cloud.pem.crt",
"keyPath": "cloud.pem.key",
"thingArn": <your Thing ARN>,
"iotHost": "<HOST_PREFIX_HERE>.iot.us-west-2.amazonaws.com",
"ggHost": "greengrass.iot.us-west-2.amazonaws.com",
"keepAlive": 600
},
"runtime": {
"cGroup": {
"useSystemd": "yes"
}
}
}
Enable Hardlink/Softlink Protection
1. If you encounter an error like Insecure configuration detected: No hardlink/softlink protection, you have to do command below, before starting Greengrass core software.
vi /etc/sysctl.conf
Modify the following items.
kernel.printk = 7 7 1 7 fs.protected_hardlinks = 1 fs.protected_symlinks = 1
2. Reload the new configuration.
sysctl -p
Run the AWS Greengrass Core Software
1. Make sure your AWS Greengrass core device is connected to the internet.
Then, start your Greengrass Core to connect it to the cloud by running:
sudo /greengrass/greengrassd start
If the Greengass daemon starts successfully you should see the following output:
Setting up greengrass daemon Validating execution environment Found cgroup subsystem: cpuset Found cgroup subsystem: cpu Found cgroup subsystem: cpuacct Found cgroup subsystem: blkio Found cgroup subsystem: memory Found cgroup subsystem: devices Found cgroup subsystem: freezer Found cgroup subsystem: net_cls Found cgroup subsystem: perf_event Found cgroup subsystem: net_prio Found cgroup subsystem: hugetlb Found cgroup subsystem: pids Starting greengrass daemon..... Greengrass daemon started with PID: 2697
2. To see if your AWS Greengrass core device is running, check that /greengrass/crash.log is empty and /greengrass/var/log/system/runtime.log has text like the following:
[INFO]-Deployment agent connected to cloud [INFO]-Subscribed to topic $aws/things/GGC_Thing-gda/shadow/update/delta [INFO]-Subscribed to topic $aws/things/GGC_Thing-gda/shadow/get/accepted
This text means that your AWS Greengrass core device is connected to AWS IoT and waiting for a deployment to take place.
3. Open the AWS IoT console and check the Dashboard page. You should see the connections status.
PS. The date & time are not matched in Week mode. You can switch to Day or Hour for correct records.