Difference between revisions of "AIMLinux/AddOn/DeviceOn"
Daniel.hung (talk | contribs) |
Darren.huang (talk | contribs) |
||
| (35 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
= <span style="color:#0070c0">DeviceOn</span> = | = <span style="color:#0070c0">DeviceOn</span> = | ||
| − | This section describes the information about DeviceOn on RISC platform. | + | This section describes the information about How to install the DeviceOn on RISC platform. |
| − | == <span style="color:#0070c0"> | + | == <span style="color:#0070c0">Get the following required files from PM or AE members </span> == |
| − | + | *'''WISE-Agent''' | |
| − | + | **EX: wise-agent-Poky_3.0.4-imx8-1.4.31.0.run | |
| − | + | *'''CreateAccount''' | |
| − | + | **EX: createaccount_2020_04_10_a59cbe72.tar.gz | |
| − | + | *'''Service-SD'''K | |
| − | + | **EX: Service-SDK_Release_20200421_fsl_imx8_yocto_3f5ea785.tar.gz | |
| − | + | *'''SUSI-IoT''' | |
| − | + | **EX: SusiIoT_Release_2021_08_31_Poky_3.0.4-imx8_x64_16490.tar.gz | |
| − | + | *'''SUSI 4.0''' | |
| − | + | **EX: SUSI4.0_Release_2021_10_29_Poky_3.0.4-imx8_x64_16557.tar.gz | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== <span style="color:#0070c0">Bundle Mechanism</span> == | == <span style="color:#0070c0">Bundle Mechanism</span> == | ||
| − | + | Install the DeviceOn function on a specific BSP official release with related DeviceOn packages enabled. | |
| − | + | == <span style="color:#0070c0">DeviceOn Installation</span> == | |
| − | '''1. Install | + | === '''1. Install WISE-Agent''' === |
| − | + | ./wise-agent-Poky_xxx.run | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
During the installation, do not configure at this moment. | During the installation, do not configure at this moment. | ||
| Line 65: | Line 32: | ||
* Do you want to start RMM Agent now? [y/n](default: y) '''<span style="color:#DD0000">n</span>''' | * Do you want to start RMM Agent now? [y/n](default: y) '''<span style="color:#DD0000">n</span>''' | ||
| − | '''2. Install CreateAccount''' | + | === '''2. Install CreateAccount''' === |
Get CreateAccount program and install with npm. | Get CreateAccount program and install with npm. | ||
| − | + | tar -zxvf createaccount_xxx.tar.gz | |
| − | + | cd createaccount | |
| − | cd createaccount | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
cp -a * /usr/local/AgentService/ | cp -a * /usr/local/AgentService/ | ||
| − | '''3. Set up Zero-Config service''' | + | === '''3. Set up Zero-Config service''' === |
| − | |||
| − | |||
| − | + | ==== '''[System V]''' ==== | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Create the "zero-config" file, and the content of zero-config: | |
#!/bin/sh | #!/bin/sh | ||
| Line 120: | Line 74: | ||
exit 0 | exit 0 | ||
| − | + | Set up the zero-config file: | |
| + | |||
| + | cp zero-config /etc/init.d | ||
| + | chown root:root /etc/init.d/zero-config | ||
| + | chmod 0750 /etc/init.d/zero-config | ||
| + | update-rc.d -f zero-config remove | ||
| + | update-rc.d zero-config defaults 99 20 | ||
| − | + | ==== '''[System D]''' ==== | |
| − | |||
| − | |||
| − | |||
| − | + | Create the "zero-config.service" file, and the content of zero-config.service: | |
[Unit] | [Unit] | ||
| Line 145: | Line 102: | ||
WantedBy=multi-user.target | WantedBy=multi-user.target | ||
| − | + | Set up the zero-config.service file: | |
| − | + | cp zero-config.service /etc/systemd/system | |
| + | chown root:root /etc/systemd/system/zero-config.service | ||
| + | chmod 750 /etc/systemd/system/zero-config.service | ||
| + | systemctl enable zero-config.service | ||
| − | + | === '''4. Install Service-SDK''' === | |
| − | |||
| − | |||
| − | |||
| − | + | tar -zxvf Service-SDK_Release_xxx.tar.gz | |
| + | cp -a Service-SDK/.libs/libEIServiceSDK.so* /usr/lib/ | ||
| − | + | === '''5. Install SUSI-IoT''' === | |
| − | + | tar -zxvf SusiIoT_Release_xxx.tar.gz | |
| + | cd release/library | ||
| + | sudo ./install.sh | ||
| − | + | === '''6. Install SUSI 4.0''' === | |
| − | |||
| − | |||
| − | |||
| − | |||
| + | tar -zxvf SUSI4.0_Release_xxx.tar.gz | ||
cd SUSI4.x.x/Driver | cd SUSI4.x.x/Driver | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
sudo ./install.sh | sudo ./install.sh | ||
''PS. Please make sure the owner of files above are ''''root:root''''.'' | ''PS. Please make sure the owner of files above are ''''root:root''''.'' | ||
| − | + | == <span style="color:#0070c0">First Boot</span> == | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Connect the internet and during the first boot procedure, the /usr/local/AgentService/agent_config.xml will be updated by saagent service firstly. The MAC address is used as an unique device id for DeviceOn. | |
<DeviceName>imx6dlubc220a1</DeviceName> | <DeviceName>imx6dlubc220a1</DeviceName> | ||
| Line 229: | Line 165: | ||
[[File:Deviceon home.png|800px|deviceon_home]] | [[File:Deviceon home.png|800px|deviceon_home]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
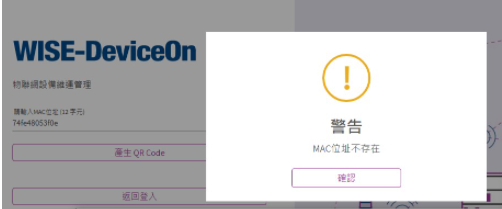
| − | + | If the '''[https://deviceonapp.wise-paas.com/#/DeviceQRCode DeviceQRCode]''' website appear the mac address does not exist, the mac account may have expired (six month trial period) or '''you can check the <IoTKey> exist or not in the /usr/local/AgentService/agent_config.xml'''. | |
| − | + | '''''If the <IoTKey> is empty, please connect the internet and reboot the device agai''n'''. | |
| − | + | [[File:Deviceon mac.png|800px|Deviceon_mac]] | |
| − | DeviceOn | + | == <span style="color:#0070c0">DeviceOn logs and check the connection</span> == |
| + | You can go to the /usr/local/AgentService/logs and check the log file: | ||
| − | + | 04-01 07:35:11.306 1687 [WiseAgent] Agent Credential: mqtt,efcc749121b5ecd182f58aa1649457eb_created,2265409aaecb11bf79a7c16473af5c47,deviceonapp.wise-paas.com,1883,false | |
| − | + | 04-01 07:35:11.306 1687 [WiseAgent] Connecting to broker: deviceonapp.wise-paas.com | |
| − | + | 04-01 07:35:11.389 1740 [WiseAgent] Broker connected! | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 10:21, 1 April 2022
Contents
DeviceOn
This section describes the information about How to install the DeviceOn on RISC platform.
Get the following required files from PM or AE members
- WISE-Agent
- EX: wise-agent-Poky_3.0.4-imx8-1.4.31.0.run
- CreateAccount
- EX: createaccount_2020_04_10_a59cbe72.tar.gz
- Service-SDK
- EX: Service-SDK_Release_20200421_fsl_imx8_yocto_3f5ea785.tar.gz
- SUSI-IoT
- EX: SusiIoT_Release_2021_08_31_Poky_3.0.4-imx8_x64_16490.tar.gz
- SUSI 4.0
- EX: SUSI4.0_Release_2021_10_29_Poky_3.0.4-imx8_x64_16557.tar.gz
Bundle Mechanism
Install the DeviceOn function on a specific BSP official release with related DeviceOn packages enabled.
DeviceOn Installation
1. Install WISE-Agent
./wise-agent-Poky_xxx.run
During the installation, do not configure at this moment.
* Setup Agent [y/n](default:n): y * Do you want to configure RMM Agent now? [y/n](default: y) n * Do you want to start RMM Agent now? [y/n](default: y) n
2. Install CreateAccount
Get CreateAccount program and install with npm.
tar -zxvf createaccount_xxx.tar.gz cd createaccount cp -a * /usr/local/AgentService/
3. Set up Zero-Config service
[System V]
Create the "zero-config" file, and the content of zero-config:
#!/bin/sh
SERVICE_PATH="/usr/local/AgentService/"
SERVICE_PROGRAM="node index.js"
# Source function library.
. /etc/init.d/functions
case "$1" in
start)
echo -n "Starting CreateAccount: "
cd $SERVICE_PATH
$SERVICE_PROGRAM > /dev/null 2>&1
RETVAL=$?
if [ $RETVAL -eq 0 ]; then
echo "OK"
else
echo "Failure"
fi
;;
*)
echo "Usage: $0 {start}"
exit 1
;;
esac
exit 0
Set up the zero-config file:
cp zero-config /etc/init.d chown root:root /etc/init.d/zero-config chmod 0750 /etc/init.d/zero-config update-rc.d -f zero-config remove update-rc.d zero-config defaults 99 20
[System D]
Create the "zero-config.service" file, and the content of zero-config.service:
[Unit] Description=CreatAccount After=saagent.service [Service] User=root Group=root Type=idle WorkingDirectory=/usr/local/AgentService/ ExecStartPre=/bin/sleep 10 ExecStart=/usr/bin/node /usr/local/AgentService/index.js [Install] WantedBy=multi-user.target
Set up the zero-config.service file:
cp zero-config.service /etc/systemd/system chown root:root /etc/systemd/system/zero-config.service chmod 750 /etc/systemd/system/zero-config.service systemctl enable zero-config.service
4. Install Service-SDK
tar -zxvf Service-SDK_Release_xxx.tar.gz cp -a Service-SDK/.libs/libEIServiceSDK.so* /usr/lib/
5. Install SUSI-IoT
tar -zxvf SusiIoT_Release_xxx.tar.gz cd release/library sudo ./install.sh
6. Install SUSI 4.0
tar -zxvf SUSI4.0_Release_xxx.tar.gz cd SUSI4.x.x/Driver sudo ./install.sh
PS. Please make sure the owner of files above are 'root:root'.
First Boot
Connect the internet and during the first boot procedure, the /usr/local/AgentService/agent_config.xml will be updated by saagent service firstly. The MAC address is used as an unique device id for DeviceOn.
<DeviceName>imx6dlubc220a1</DeviceName> <DevID>00000001-0000-0000-0000-00049F0130E0</DevID> <SN>00049F0130E0</SN> <UserName>00049F0130E0@advtrial.net</UserName>
Then, zero-config service will register this account to the server. Once successful, the agent_config.xml will be updated again with corresponding credentials.
<CredentialURL>https://deviceonapp.wise-paas.com/rmm/v1/iothub/credential</CredentialURL> <IoTKey>10da34e72025c137618bb4d4aefff18d</IoTKey>
These procedures are automatically complete during first booting up. Users only need to power up device and connect with network.
Connect to Server
On PC or cellular phone, connect to DeviceQRCode website and input the MAC address of your target device.
If your target device has multiple Ethernet interfaces, use the following command to confirm the associated MAC.
$ cat /usr/local/AgentService/agent_config.xml | grep SN <SN>00049F0130E0</SN>
Follow the steps to connect to DeviceOn server
1. Click the button to generate QR code
2. Click the QR code or scan it with camera
The QR code will re-direct to DeviceOn home page. Enjoy it!
If the DeviceQRCode website appear the mac address does not exist, the mac account may have expired (six month trial period) or you can check the <IoTKey> exist or not in the /usr/local/AgentService/agent_config.xml.
If the <IoTKey> is empty, please connect the internet and reboot the device again.
DeviceOn logs and check the connection
You can go to the /usr/local/AgentService/logs and check the log file:
04-01 07:35:11.306 1687 [WiseAgent] Agent Credential: mqtt,efcc749121b5ecd182f58aa1649457eb_created,2265409aaecb11bf79a7c16473af5c47,deviceonapp.wise-paas.com,1883,false 04-01 07:35:11.306 1687 [WiseAgent] Connecting to broker: deviceonapp.wise-paas.com 04-01 07:35:11.389 1740 [WiseAgent] Broker connected!