Difference between revisions of "Ingress with the wildcard ssl certificate of Lets Encrypt on AKS"
Fred.chang (talk | contribs) |
Fred.chang (talk | contribs) |
||
| Line 38: | Line 38: | ||
== Configuration == | == Configuration == | ||
| + | |||
| + | *You can modify the file '''"route.yaml"''' to fit your scenario, and apply it by using '''"kubectl apply -f route.yaml"'''. | ||
Revision as of 07:17, 12 July 2019
Prerequisite
1. Have an Azure DNS Zone and delegate your domain name into it. (refer to Host your domain in Azure DNS)
2. Have an AKS and make sure it's Linux-based.
3. Note down the name($AKS_NAME) and resource group($AKS_RESOURCE_GROUP) of the AKS.
First thing on Azure
1. Please refer to Quickstart for Bash in Azure Cloud Shell and enter the azure bash.
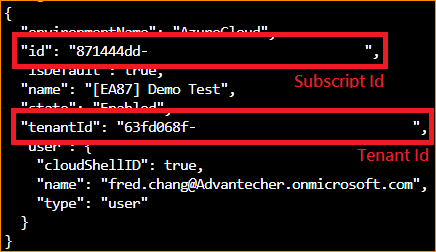
2. Show you account information by using "az account show" and note down your subscription id($SUBSCRIPTION_ID) and tenant id($TENANT_ID) be shown as the following picture.
3. Use "az aks get-credentials --resource-group $AKS_RESOURCE_GROUP --name $AKS_NAME" to get the access right of kubectl.
4. Make sure that you have the capability to install packages with helm. If not, please refer to Install applications with Helm in Azure Kubernetes Service (AKS)
Upload and Execute
1. Download File:AKSLE.zip.
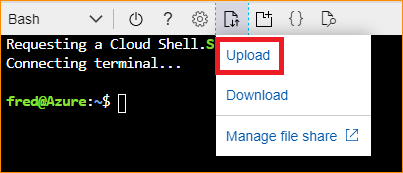
2. Unzip it and upload AKSLE.sh as the following picture.
3. Change the file mode by using "chmod 777 AKSLE.sh"
4. Execute it and it will generate a file "route.yaml".
'AKSLE.sh $DOMAIN_NAME $ADMIN_EMAIL_ADDRESS $SUBSCRIPTION_ID $TENANT_ID'
Example: 'AKSLE.sh "edgecenter.io" "fred.chang@advantech.com.tw" "12345679-1234-1234-1234-123456789012" "abcdefgh-abcd-abcd-abcd-abcdefghijkl"'
5. Show EXTERNAL-IP by using 'kubectl get service/nginx-ingress-controller' and update it on Azure DNS zone.
Configuration
- You can modify the file "route.yaml" to fit your scenario, and apply it by using "kubectl apply -f route.yaml".