Difference between revisions of "WISE-PaaS/Single Sign-On(SSO)"
From ESS-WIKI
Dylan.chang (talk | contribs) |
Dylan.chang (talk | contribs) |
||
| Line 66: | Line 66: | ||
WISE-PaaS provides a complete service for Single Sign-On. There are tree sections for developer to implement. | WISE-PaaS provides a complete service for Single Sign-On. There are tree sections for developer to implement. | ||
| − | + | #'''Settings on Authorization Server''' | |
| − | + | #* Apply a manager account for OpenID Central Server. ''Please sen a request to [mailto:Jonathan.Lin@advantech.com.tw WISE-Paas/OpenID Connect service manager] by E-mail. And provide the following information'' | |
| − | + | #**''''Service name : [''RMM''] as your realm. | |
| − | + | #**Client name : [''RMMClient''] a client definition for a app to login in. | |
| − | ''Please sen a request to [mailto:Jonathan.Lin@advantech.com.tw WISE-Paas/OpenID Connect service manager] by E-mail. And provide the following information'' | + | #**User registration : [''True/False''] Enable/Disable user registeration. |
| − | + | #**Administrator account : [''RMMAdmin''] Use this account to manage this realm. The default password is same as account name. Change password after first login | |
| − | *Service name : [''RMM''] as your realm. | + | #*Setting your service on Single Sign-On server |
| − | *Client name : [''RMMClient''] a client definition for a app to login in. | + | #**Login Single Sign-On server |
| − | *User registration : [''True/False''] Enable/Disable user registeration. | + | #**Authorization Setting |
| − | *Administrator account : [''RMMAdmin''] Use this account to manage this realm. The default password is same as account name. Change password after first login | + | #**#Authorization Enabled. |
| − | + | #**#Create a Resource : Creating the resources that you want to protect. | |
| − | + | #**#Create a Permission : A permission associates the object being protected and the policies that must be evaluated to decide whether access should be granted. | |
| − | + | #**#Create a Role : Use this type of policy to define conditions for your permissions where a set of one or more roles is permitted to access an object. | |
| − | + | #**#Create a User : Craete a login account for SSO with role mapping of client. | |
| − | + | #**#Evaluate : When designing your policies, you can simulate authorization requests to test how your policies are being evaluated with a json format result. | |
| − | + | #**Get Client App setting | |
| − | + | #**#Realm Public Key : Get the public key from Realms setting-> [''Realm'']->Keys-> Public key. | |
| − | #Authorization Enabled | + | #**#Client Credentials Secret : Get Secret from Clients->Credentials->Secret |
| − | #Create a Resource : Creating the resources that you want to protect | + | #'''Application for end user''' |
| − | #Create a Permission : A permission associates the object being protected and the policies that must be evaluated to decide whether access should be granted. | + | #*''Copy the json , html sample code to your local web site.'' |
| − | #Create a Role : Use this type of policy to define conditions for your permissions where a set of one or more roles is permitted to access an object. | + | #*''Modify json setting'' |
| − | #Create a User : Craete a login account for SSO with role mapping of client. | + | #*''Once the test HTML page is opened, it is automatically directed to OpenID Connect Server.'' |
| − | #Evaluate : When designing your policies, you can simulate authorization requests to test how your policies are being evaluated with a json format result. | + | #*While login success, it will automatically lead back to test page. |
| − | + | #'''Verify Access Token on Resource Server''' | |
| − | |||
| − | |||
| − | #Realm Public Key : Get the public key from Realms setting-> [''Realm'']->Keys-> Public key. | ||
| − | #Client Credentials Secret : Get Secret from Clients->Credentials->Secret | ||
| − | |||
| − | |||
| − | |||
| − | #''Copy the json , html sample code to your local web site.'' | ||
| − | #''Modify json setting'' | ||
| − | #''Once the test HTML page is opened, it is automatically directed to OpenID Connect Server.'' | ||
| − | #While login success, it will automatically lead back to test page. | ||
| − | |||
| − | |||
== Document == | == Document == | ||
Revision as of 07:48, 16 January 2017
Single Sign-On (SSO) is part of Advantech WISE-PaaS cloud solution and plays an important role in the interoperability of Internet identity. It provides a central login mechanism.
OpenID Connect utilizes Keycloak which is an open source identity and access management for modern applications and services.
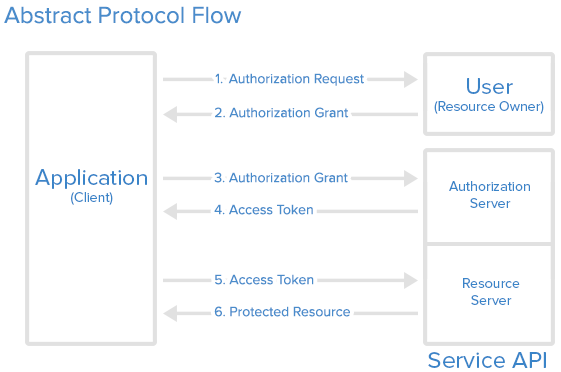
API Protocol Flow
WISE-PaaS/Single Sign-On use the OAuth 2.0 protocol for authentication and authorization.
- User/Resource owner : Who authorizes others to access Protected Resource. If the role is human, it means the end-user.
- Application/Client/Browse : An application ,client or a browser page represents the Resource Owner to access the Protected Resource.
- Authorize Server : The server issues the Access Token after user are authenticated. (WISE-PaaS/Single Sign-On server)
- Resource Server : The server hosting Protected Resource accept requests according to Access Token.
Here is a more detailed explanation of the steps in the diagram:
- The application requests authorization to access service resources from the user
- If the user authorized the request, the application receives an authorization grant
- The application requests an access token from the authorization server (API) by presenting authentication of its own identity, and the authorization grant
- If the application identity is authenticated and the authorization grant is valid, the authorization server (API) issues an access token to the application. Authorization is complete.
- The application requests the resource from the resource server (API) and presents the access token for authentication
- If the access token is valid, the resource server (API) serves the resource to the application
Features Overview
WISE-PaaS/Single Sign-On(SSO) which base on keycloak has the following features.
- Single-Sign On : Login once to multiple applications
- Standard Protocols : OpenID Connect, OAuth 2.0 and SAML 2.0
- Centralized Management : For admins and users
- Adapters : Secure applications and services easily
- High Performance : Lightweight, fast and scalable
- Clustering : For scalability and availability
- Themes : Customize look and feel
- Extensible : Customize through code
- Password Policies : Customize password policies
Components
[Please describe]
- OpenID Connect Server
- OpenID Connect Client
- OAuth 2.0 Server
- OAuth 2.0 Client
Implementation
WISE-PaaS provides a complete service for Single Sign-On. There are tree sections for developer to implement.
- Settings on Authorization Server
- Apply a manager account for OpenID Central Server. Please sen a request to WISE-Paas/OpenID Connect service manager by E-mail. And provide the following information
- Service name : [RMM] as your realm.
- Client name : [RMMClient] a client definition for a app to login in.
- User registration : [True/False] Enable/Disable user registeration.
- Administrator account : [RMMAdmin] Use this account to manage this realm. The default password is same as account name. Change password after first login
- Setting your service on Single Sign-On server
- Login Single Sign-On server
- Authorization Setting
- Authorization Enabled.
- Create a Resource : Creating the resources that you want to protect.
- Create a Permission : A permission associates the object being protected and the policies that must be evaluated to decide whether access should be granted.
- Create a Role : Use this type of policy to define conditions for your permissions where a set of one or more roles is permitted to access an object.
- Create a User : Craete a login account for SSO with role mapping of client.
- Evaluate : When designing your policies, you can simulate authorization requests to test how your policies are being evaluated with a json format result.
- Get Client App setting
- Realm Public Key : Get the public key from Realms setting-> [Realm]->Keys-> Public key.
- Client Credentials Secret : Get Secret from Clients->Credentials->Secret
- Apply a manager account for OpenID Central Server. Please sen a request to WISE-Paas/OpenID Connect service manager by E-mail. And provide the following information
- Application for end user
- Copy the json , html sample code to your local web site.
- Modify json setting
- Once the test HTML page is opened, it is automatically directed to OpenID Connect Server.
- While login success, it will automatically lead back to test page.
- Verify Access Token on Resource Server