DeviceOn/ePaper
A surge in market demand for Industrial IoT products has rapidly increased the number of connected devices that are currently deployed and managed across different locations. It is essential to effectively manage, monitor, and control thousands of connected EPD devices while ensuring uninterrupted service. EPD Devices must work properly and securely after they have been deployed - without requiring frequent visits from service technicians. Customers require secure access to their devices in order to detect, troubleshoot, and undertake time-critical actions.
Contents
What’s DeviceOn/ePaper?
DeviceOn/ePaper is a software platform developed by Advantech, a global leader in industrial computing solutions. It is designed to manage ePaper displays, which are electronic paper displays that can be updated remotely and display information. EPD Device optimizes power consumption through two-way communication and realizes device roaming, reliable communication security, and information display.
- Solution
- DeviceOn/ePaper Server provides a centralized platform for managing ePaper displays across multiple locations, allowing users to update content, monitor display status, and configure display settings from a single interface. It supports a wide range of ePaper display models and sizes, and can be integrated with existing content management systems.
- Integration
- The EPD device can be applied to different applications and system integrators can control the RESTful APIs to design for different scenarios.
Overall, DeviceOn/ePaper Server is a powerful tool for businesses and organizations that need to manage large numbers of ePaper displays across multiple locations. It provides a streamlined and efficient way to update content, monitor display status, and ensure that information is being displayed accurately and consistently. Details: System Architecture
Feature Highlight
Some of the key features of DeviceOn/ePaper Server include:
- Remote management of ePaper displays
- Real-time display status monitoring
- Support for multiple display models and sizes
- Integration with existing content management systems
- Customizable display templates and layouts
- Automatic content scheduling and delivery
- User access control and permission management
DeviceOn/ePaper Solutions
| ePaper Models | ||||||
|
Security
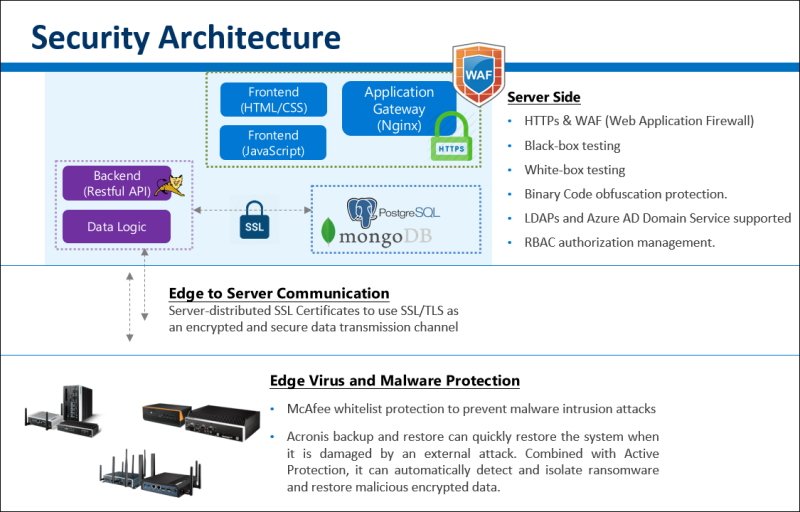
System Security is about not only installing and onboarding devices and networks securely but also managing their ongoing operations throughout their lifecycle and identifying and isolating any threats. Industries everywhere are digitizing, which is creating a multitude of new security requirements for the Internet of Things (IoT). End-to-end (E2E) security management will be essential to ensuring security and privacy in the IoT, while simultaneously building strong identities and maintaining trust. As the diversity of IoT services and the number of connected devices continue to increase, the threats to IoT systems are changing and growing even faster.
A comprehensive model of IoT device security, as shown in below structure, the comprehensive IoT module security in an IoT system has three main parts:
1. Device Security
DeviceOn/ePaper Server leverage McAfee Embedded Security software to prevents unauthorized changes and will lock a system down to a known application is an industry, that’s an industrial first solution to secure embedded devices. For disaster recovery, Acronis provides users a quick and easy-operated solution to protect data and recover the entire system even when OS crash, effectively reduces down-time cost and lowers the risk of data loss. In the Zigbee solution at the edge, during the EPD device joining the network, the EPD router uses EPID (Extended PAN ID) to create a private network to filter non-EPD devices. EPD device is a wireless microcontroller unit (MCU). It has a built-in hardware accelerator for the Advanced Encryption Standard (AES) algorithm, which is commonly used for secure data communication over wireless networks. The encryption protocol of the Wi-Fi solution is WPA2 (Wi-Fi Protected Access 2), which provides encryption to protect data from being intercepted or tampered with during transmission.
2. Secure Transporty
The server distributed SSL certificates to use TLS (v-1.3) as an encrypted and secure data transmission channel, and device default enable MQTT-SSL for communication.
- Topics Isolation & Unique Device IoT Key
- Topics are specially handled in RabbitMQ. Topics are not public. Access control isolates an activated device to publishing/subscribing only to that device’s topics even though multiple devices will have subscriptions to identically named topics. A device is not allowed to subscribe/publish to another device’s topics.
- Second, in IoT applications, command topics are used to control a device remotely and to acknowledge successful command executions. Unlike telemetry, command topics are not read-only. Commands are a back and forth workflow that can occur between the cloud and devices. Because commands are actionable messages, isolate the MQTT topic for command messages from telemetry topics.
- Use x.509 Certificates to Authenticate Edge Device
- DeviceOn/ePaper supports x.509 certificate authentication for use with a secure TLS/SSL connection. The x.509 edge device authentication allows device to authenticate to servers with certificates rather than with a username and password.
- Use TPM + x.509 Certificates to Provide Higher Security
- The solution that we integrate on DeviceOn/ePaper for Azure (Enterprise Edition), leverage Azure IoT Edge and TPM 2.0 to offer secure authentication and private key protected.
- TPM, also known as ISO/IEC 11889, is a standard for securely generating and storing cryptographic keys. TPM also refers to a virtual or physical I/O device that interacts with modules that implement the standard. A TPM device can exist as discrete hardware, integrated hardware, a firmware-based module, or a software-based module.
3. Secure Cloud Service
The cloud service components include Tomcat as a web server that provide an HTTPS protocol and backend APIs services, each connection between backend and database adopt SSL encryption, and enforce password policies. Second, for advanced attack, such as SQL injection, XXC, local and remote file vulnerabilities, the Nginx+Naxsi to achieve Web Application firewall (WAF) protection. All DeviceOn/ePaper services pass through famous vulnerability tools to ensure security for your it IoT solutions, and the binary uses ProGuard code obfuscation protection. The APIs authentication not only uses JWT (JSON Web Tokens) to hide/encrypt sensitive data, but, integrate LDAPs & Azure AD Domain Service for secure.
Role-based Access Control (RBAC)
DeviceOn/ePaper supports three different user roles - “Root”, “System Admin” and “Device Admin”. There is only one single “Root” account per system, which has the highest permission level and can create “System Admin” or “Device Admin” accounts. The intermediate user level “System Admin” can be used to create “Device Admin” accounts. “Device Admin” accounts have the lowest permission level.
SSL Encryption
- HTTPS on DeviceOn/ePaper Web Server
- The principal motivations for HTTPS are authentication of the accessed website, protection of the privacy and integrity of the exchanged data while in transit. It protects against man-in-the-middle attacks. The bidirectional encryption of communications between a client and server protects against eavesdropping and tampering of the communication.
- SSL Connection on Database (PostgreSQL, MongoDB)
- PostgreSQL and MongoDB have native support for using SSL connections to encrypt client/server communications for increased security.
- Create Security Credentials on Database
- Databases are by default protected by secure credentials and require explicit authentication for connections. This avoids accidentally deploying platforms with unprotected access.
- Device Connectivity via MQTT SSL
- RabbitMQ supports multiple protocols including MQTT, which the most popular IoT (Internet of Things) protocol. By default, SSL is used to encrypt all MQTT traffic for device connectivity.
- Enforce Password Policies
- While DeviceOn/ePaper allows you to set some of your own passwords, please make sure those meet the minimum complexity requirements established by your specific organization.
Vulnerability Scanning Tools
The DeviceOn/ePaper server pass through below famous vulnerability tools to ensure security for your AIoT solutions. Furthermore, all the testing including anti-malware (Trend Micro and Kaspersky)
- Web Application Assessment Report (Micro Focus)
- WebInspect is an automated dynamic testing tool that mimics real-world hacking techniques and attacks, and provides comprehensive dynamic analysis of complex web applications and services.
- OpenVAS (Open Vulnerability Assessment System)
- OpenVAS is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high level and low-level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
- The scanner is accompanied by a vulnerability tests feed with a long history and daily updates. This Greenbone Community Feed includes more than 50,000 vulnerability tests.
- Nessus
- Nessus is the de-facto industry standard vulnerability assessment solution for security practitioners. The latest intelligence, rapid updates, an easy-to-use interface.
- Covers an industry-leading 47,000+ vulnerabilities
- Unlimited scans at no extra cost
- Compliant with PCI, HIPPA, GLBA, CIS, NIST, and more
- OWASP ZAP
- The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications. It’s also a great tool for experienced pentesters to use for manual security testing.
- Skipfish
- Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
- Key features:
- High speed: pure C code, highly optimized HTTP handling, minimal CPU footprint – easily achieving 2000 requests per second with responsive targets.
- Ease of use: heuristics to support a variety of quirky web frameworks and mixed-technology sites, with automatic learning capabilities, on-the-fly wordlist creation, and form autocompletion.
- Cutting-edge security logic: high quality, low false positive, differential security checks, capable of spotting a range of subtle flaws, including blind injection vectors.
- Nikto
- Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
- W3af
- w3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities.
- Arachni
- Arachni is a fully featured web security scanning tool, it is based on ruby framework.It is an open source, modular and high performance tool. It comes with both command line interface as well as web based gui interface, it is highly versatile tool for security scanning purpose. It supports almost all of the popular web application such as HTML5, Java Script and AJAX etc, Additionally it is enables with multi user-multi platform collaboration.It allows you to generate reports in desired format (.txt, XML, HTML).
Third-Party Vulnerability Fixed and Updates
- OpenJRE (v-1.8.0_292-1)
- CVE-2021-42340, CVE-2022-23181, CVE-2022-29885
- Tomcat (v-9.0.63)
- CVE-2021-33037, CVE-2021-30640, CVE-2021-30639, CVE-2020-9484, CVE-2021-25329, CVE-2021-25122
- RabbitMQ (v-3.11.6), Erlang 25
- CVE-2022-37026
- PostgreSQL (v-14.2)
- CVE-2021-23214, CVE-2021-23222
- MongoDB (v-4.4.14)

